What is threat intelligence management?
Threat intelligence management involves the systematic collection, analysis, and dissemination of information about potential cybersecurity threats and risks facing an organization. It encompasses processes and technologies for gathering data from various sources, such as open-source intelligence, dark web monitoring, and internal security tools. This data is then analyzed to identify emerging threats, vulnerabilities, and attack patterns. The insights derived from threat intelligence are used to inform decision-making processes, enhance security posture, and proactively mitigate risks. Effective threat intelligence management enables organizations to stay ahead of cyber threats, strengthen their defenses, and protect against potential cyber attacks.
The challenge:
Analysts are bombarded with millions of threat data points every day from multiple sources in multiple formats. This includes external data from commercial sources, open source, industry and existing security vendors as well as data from internal sources. Each point product within their internal layers of defense, SIEM and other systems within their security infrastructure generates a massive amount of log and event data and alerts. The noise level is deafening.
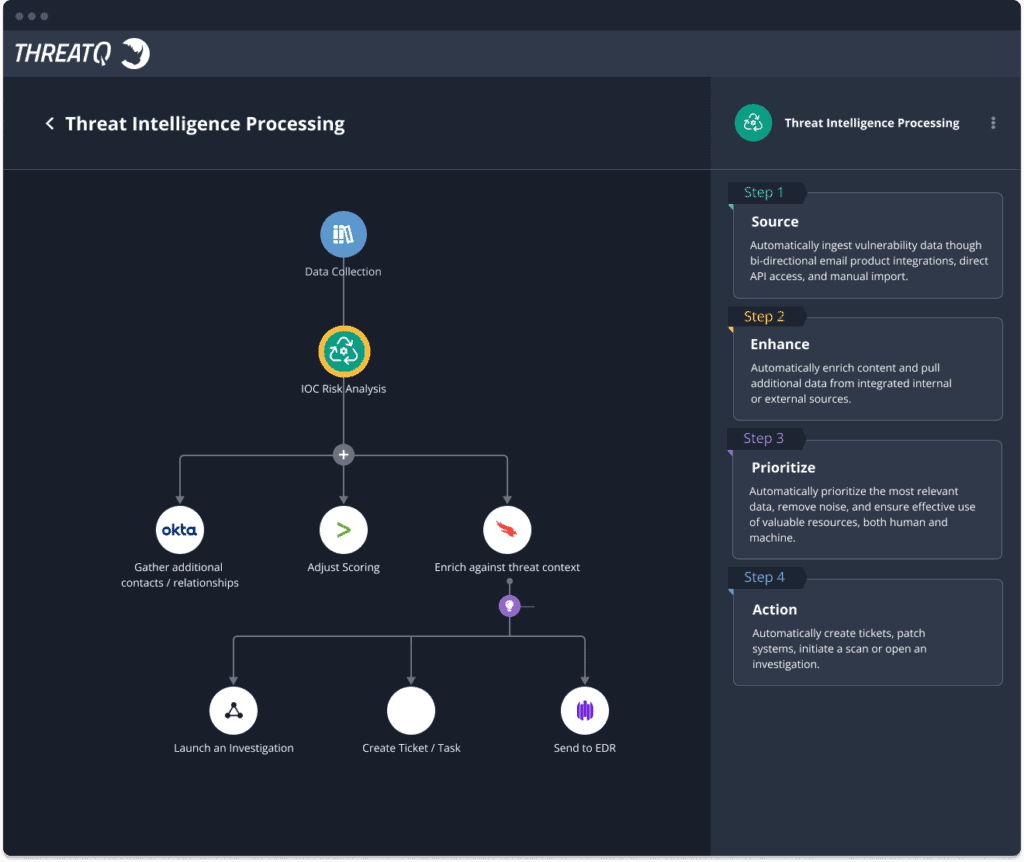
Automate threat intelligence management with ThreatQ TDR Orchestrator
ThreatQuotient’s data-driven threat intelligence platform helps to balance between human & machine focused approaches ensuring that teams always have the best tool for the job.
Learn more about ThreatQ TDR Orchestrator, the industry’s first solution to introduce a simplified, data-driven approach for no code/low code automation of alert enrichment with threat intelligence resulting in more efficient and effective security operations.
How ThreatQ meets the threat intelligence management challenge
| 1 | Connect to disparate systems and sources |
|---|---|
| 2 | Ingest and aggregate external and internal data |
| 3 | Normalize and correlate data into a single object |
| 4 | Curate and analyze data for decision making and action in threat hunting, incidence response, victimology, vulnerability management, etc. |
| 5 | Export a prioritized data flow across the infrastructure translated for improved threat detection, investigation and response. |
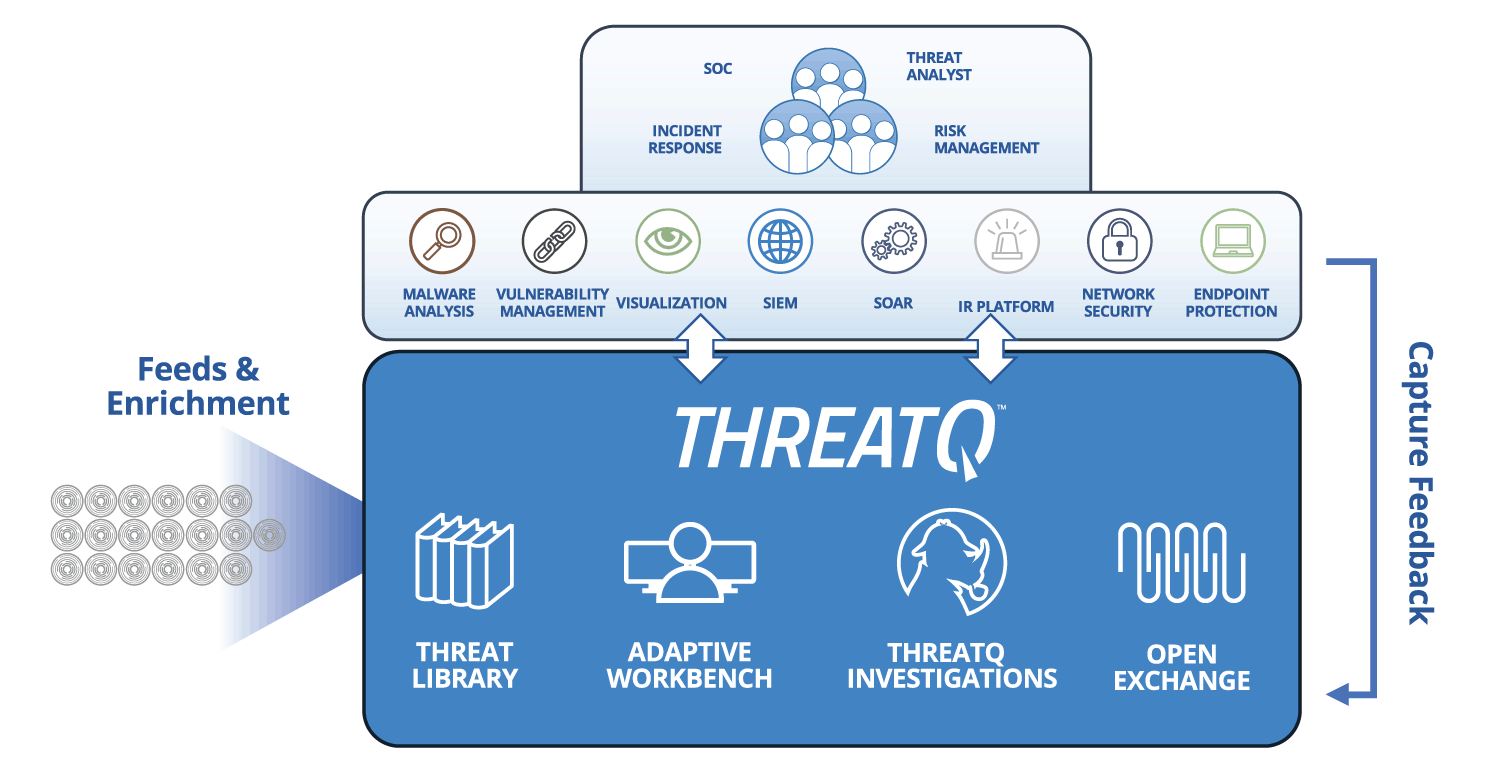
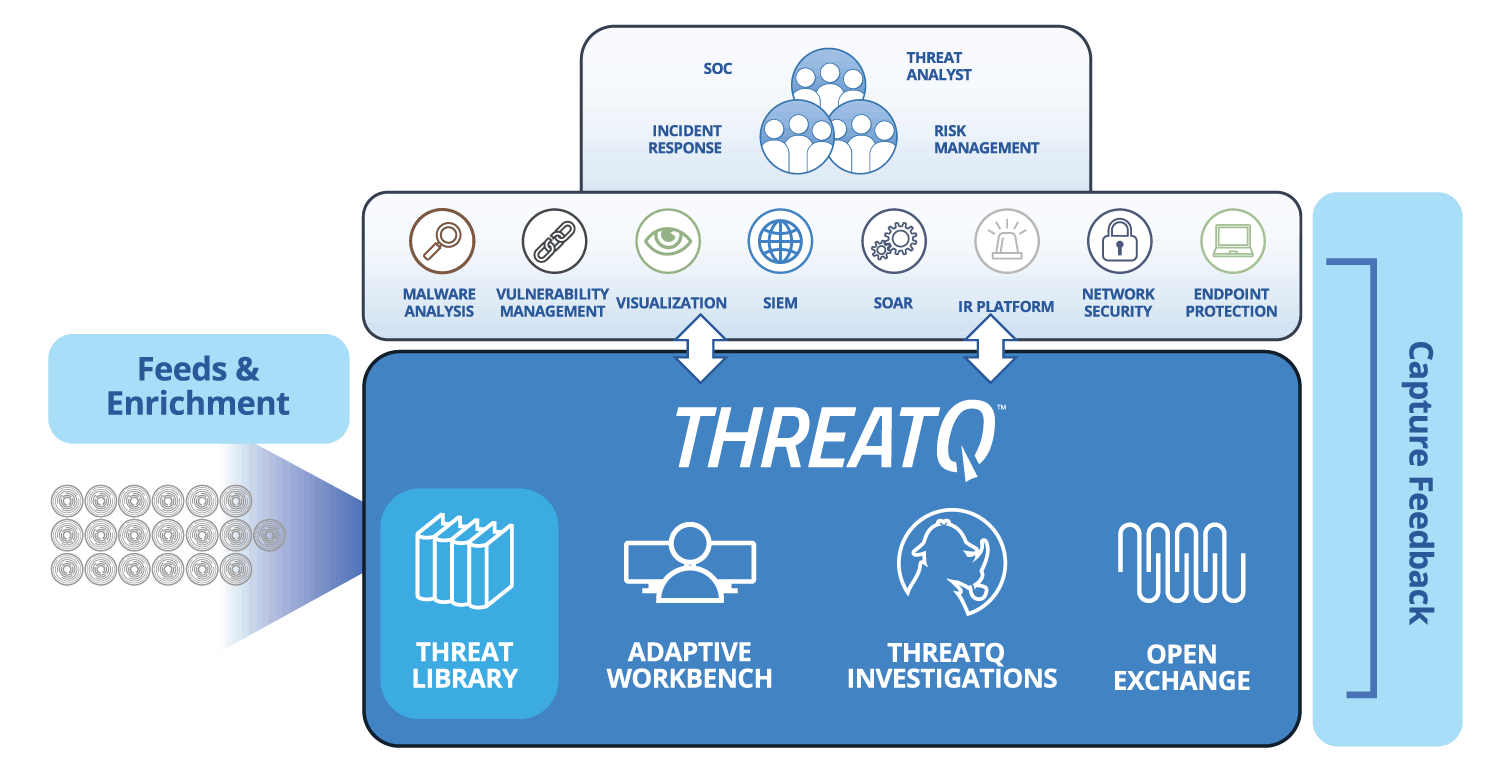
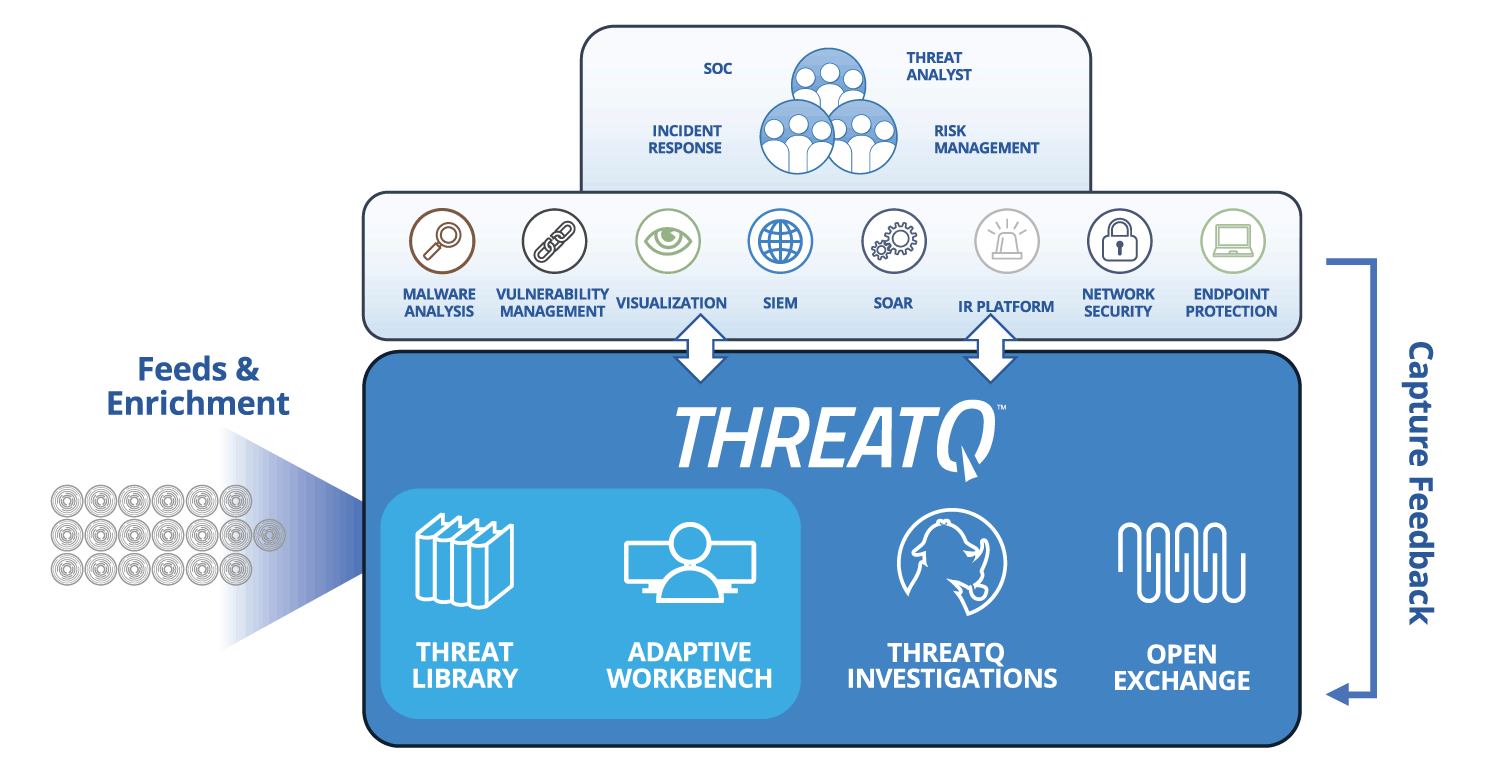
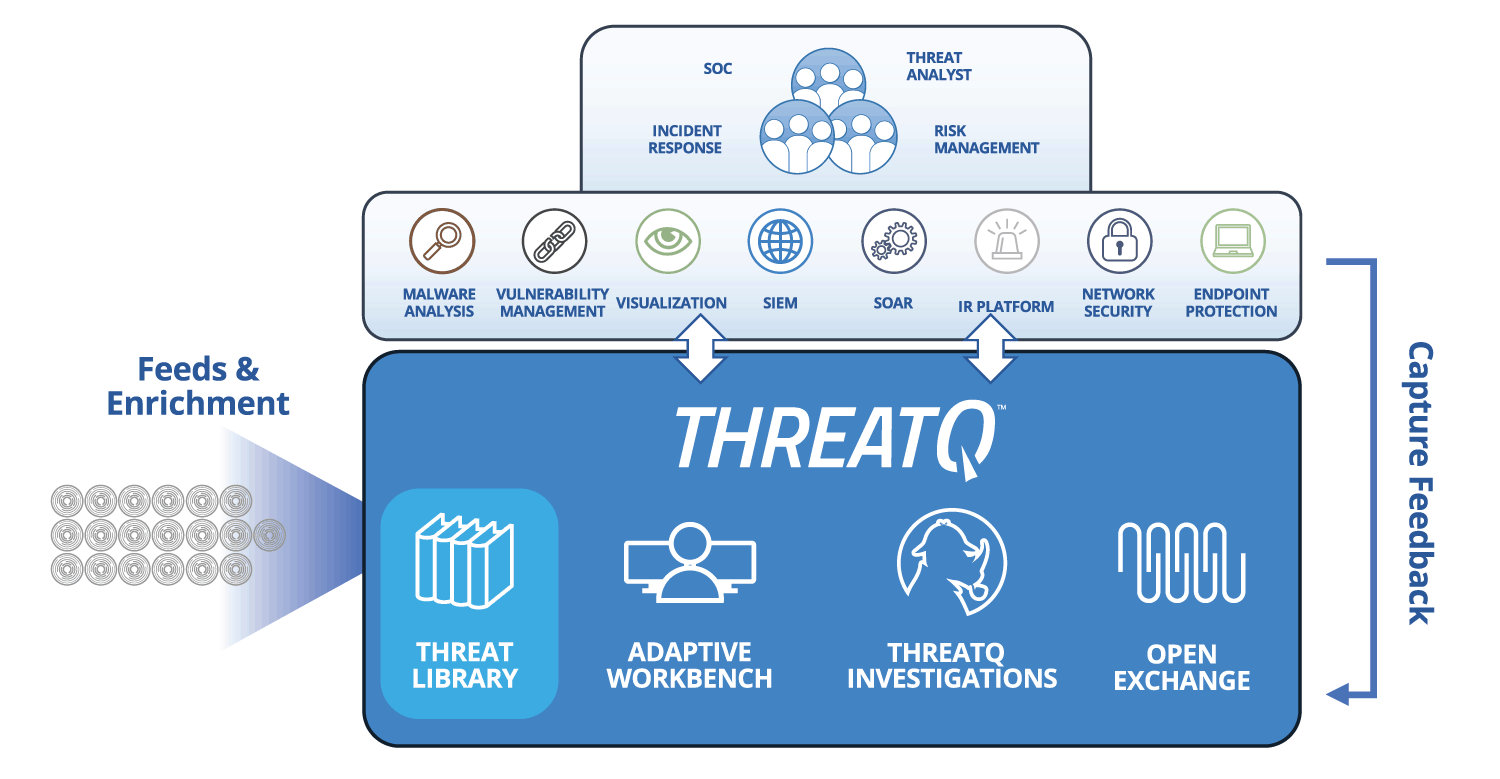
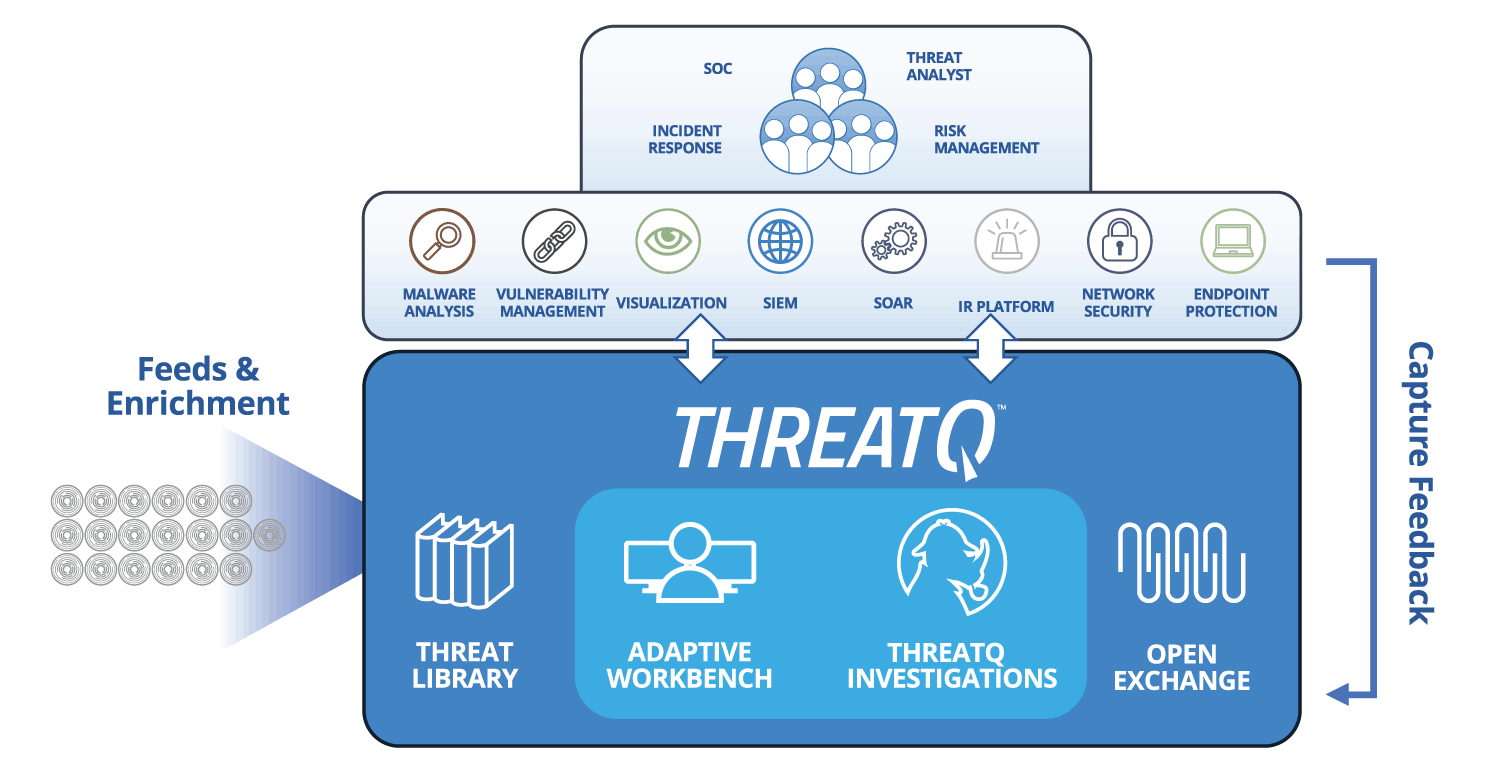
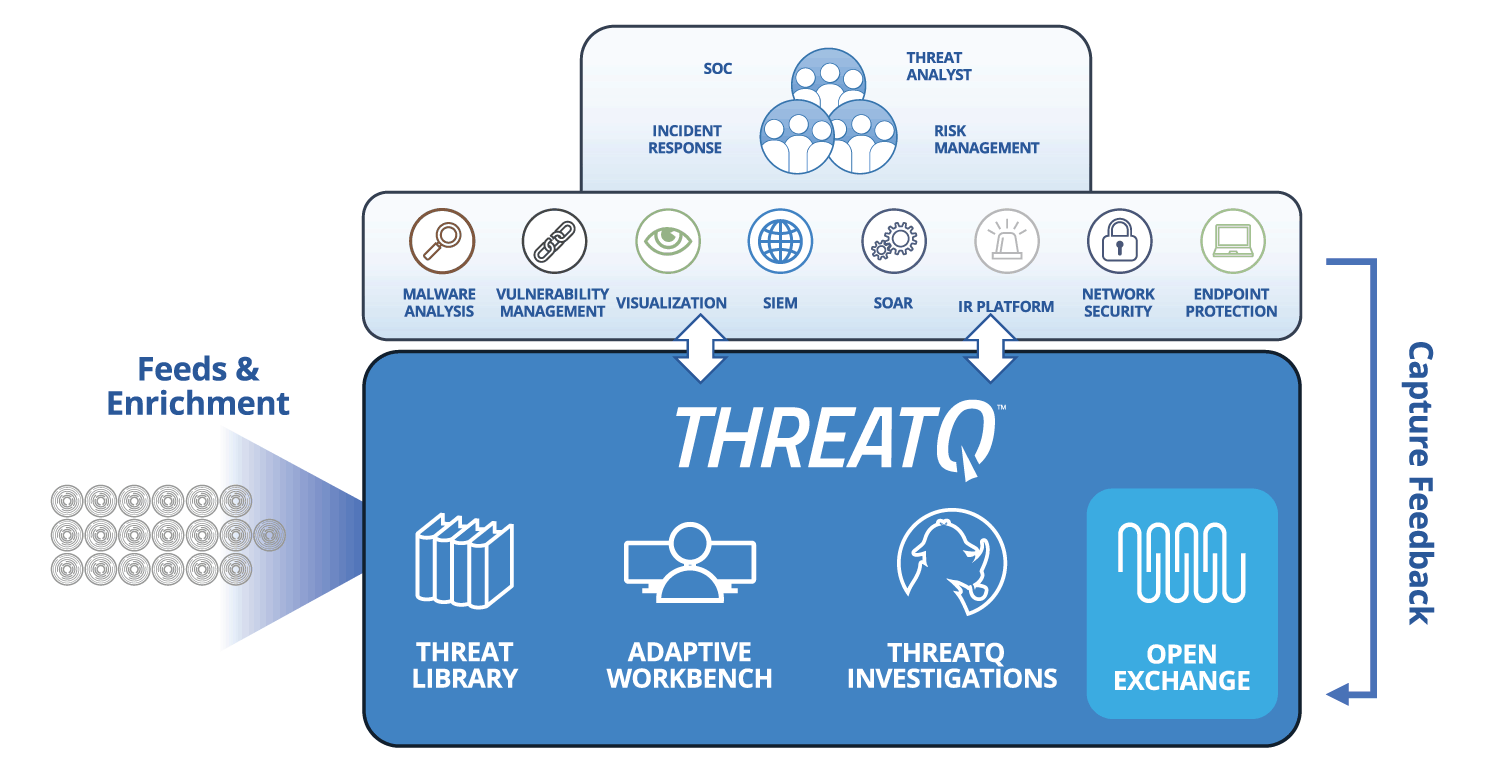
| Threat Data Aggregation | Create a single source of truth based on correlated, normalized and de-duplicated intelligence data and events across all tools and sources. Learn more > |
|---|---|
| Threat Library™ | Store global and local threat data in a central repository to provide relevant and contextual intelligence that is customized and prioritized for your unique environment. Learn More > |
| Open Exchange™ | Integrate ThreatQ with existing security tools, teams and workflows through standard interfaces to extend their value, knowledge and efficacy. Learn more > |
| Dynamic Scoring | Prioritize threat data automatically, understand why it is relevant and take action faster and with greater confidence. Learn more > |
Learn how to use ThreatQ for
threat intelligence management
Take a quick look at how threat intelligence management with ThreatQ can help you reduce noise and focus on the threat. If you like what you see, schedule a demo for a deeper dive.
The ThreatQuotient approach to threat intelligence management
Analysts need a way to automatically ingest, normalize, correlate and de-duplicate threat intelligence data in one manageable location. While this external cyber threat data is commonly well-defined and understood, additional context from within the organization can vary wildly between industry verticals and companies. It’s vital that the threat intelligence management solution be able to consume and store these different data types as well as provide the capability to tailor data models to fit security teams’ needs.
The next step is to prioritize the vast amounts of threat data aggregated in this central repository. However, what is a priority to one company may not be relevant to another. What is needed is the ability for analysts to control how scoring, prioritization and expiration should be done – tell the system what is more important and less important once, and let the system automatically score and re-score when new data and context is learned. As more data comes in, the threat intelligence management system will automatically tune itself, creating a threat library that provides consistent information tailored specifically for the company.
The repository serves as a centralized memory to facilitate future investigations. Security teams can operate from a single source of truth, passively collaborating through the instantaneous sharing of knowledge and using their tools of choice to improve security posture and reduce the window of exposure and breach.
Integration with an ecosystem of data sources is streamlined and cost effective using open APIs at no additional cost, and can be further tailored with an SDK. For broad visibility, the system must be designed to be integrated with all systems that provide or leverage threat data within the organization.
Outcomes:
- Contextualized, relevant intelligence in a database that is customized for the organization’s environment and risk profile.
- Focus, noise reduction and decision support during investigations and triage.
- Greater shared understanding of relationships across objects and object types to better support investigations and threat intelligence management.
- The freedom to spend more time performing analysis versus manual tasks.
- Orchestrated and synchronized threat intelligence management across all teams and tools so they can work in concert and increase effectiveness, efficiency and productivity.
LET’S GET STARTED!
Join the ThreatQ Community, a private community with hundreds of experienced cyber security pros sharing intel to level-up threat detection and response. Learn how ThreatQuotient can help you stay ahead of the threat.