USE CASE:
What is spear phishing?
Spear phishing is a targeted form of cyber attack where malicious actors craft personalized emails or messages to deceive specific individuals or organizations. Unlike traditional phishing attacks, which cast a wide net to lure unsuspecting victims, spear phishing involves careful research to tailor messages to the interests, roles, or relationships of the intended targets. These messages often appear legitimate and may include familiar names, logos, or information to trick recipients into divulging sensitive information, such as passwords or financial data, or to download malware. Spear phishing attacks rely on social engineering tactics to exploit human vulnerabilities and can result in significant data breaches or financial losses.
The challenge:
Spear phishing emails contain a wealth of hidden evidence that can be used to track and understand the methods used by attackers to target the organization. By extracting that information, analysts can better understand what to look for to identify other users that may have succumbed to the trick.
Armed with this evidence, analysts can discover associations between multiple spear phishing messages to understand a wider campaign that can be underway. Identifying malware samples across campaigns, and associating them with adversary profiles (and therefore intentions) notably improves the ability to respond.
Conducting this level of analysis can be difficult and laborious. Typically, analysts must discover these associations by manually sifting through messages and correlating the information they discover about the campaign with external data on adversaries and their methods.
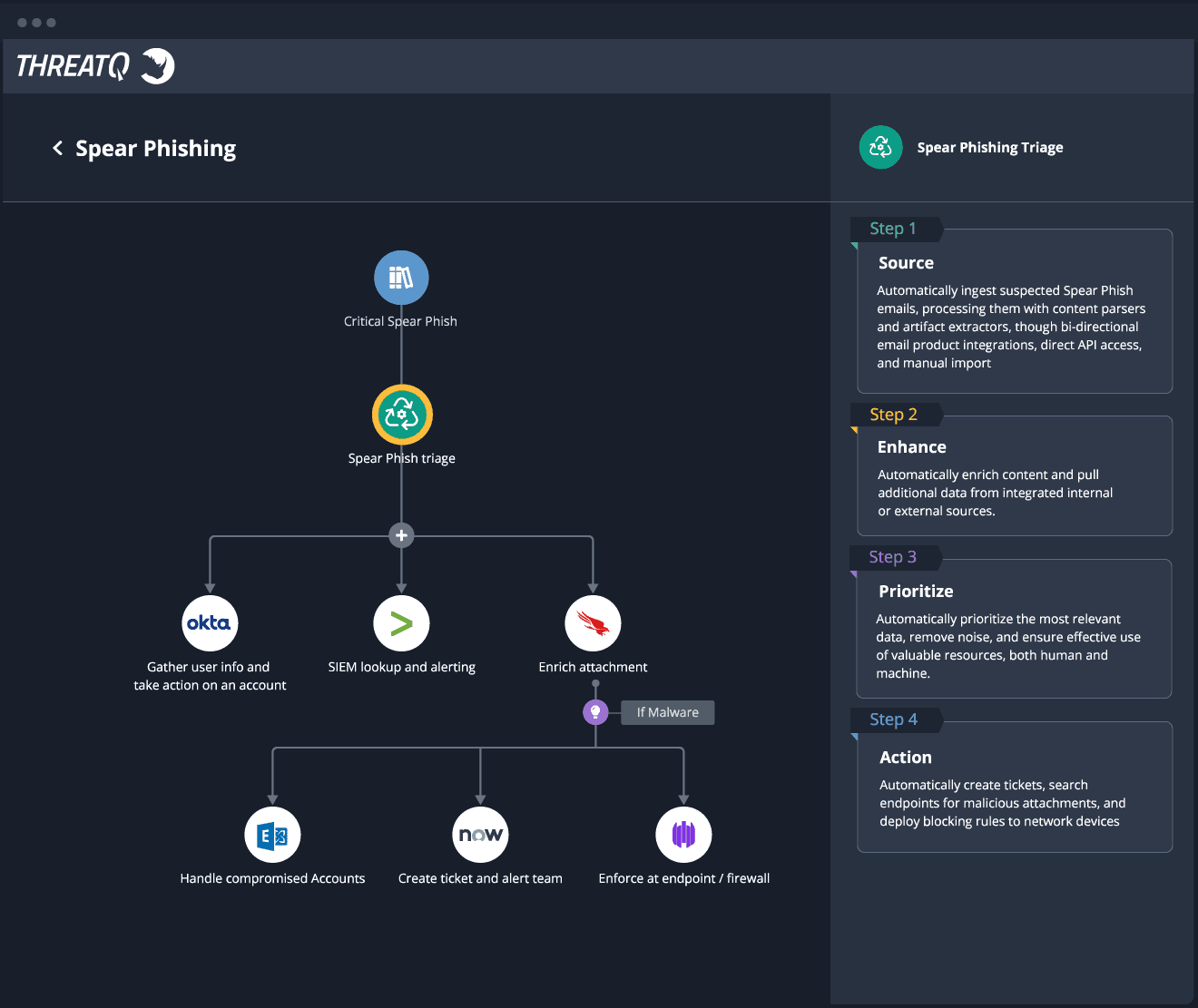
Automate spear phishing triage with ThreatQ TDR Orchestrator
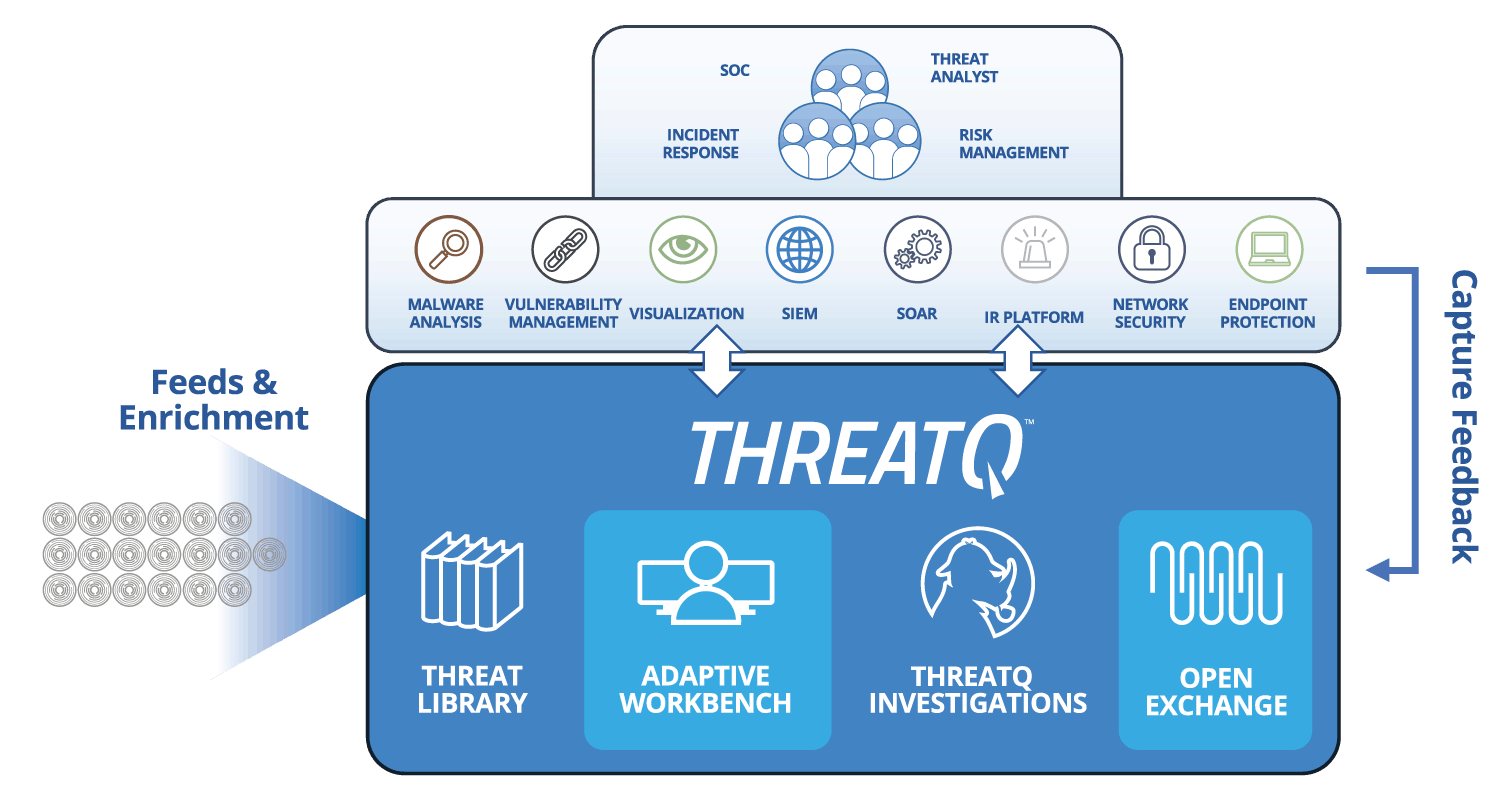
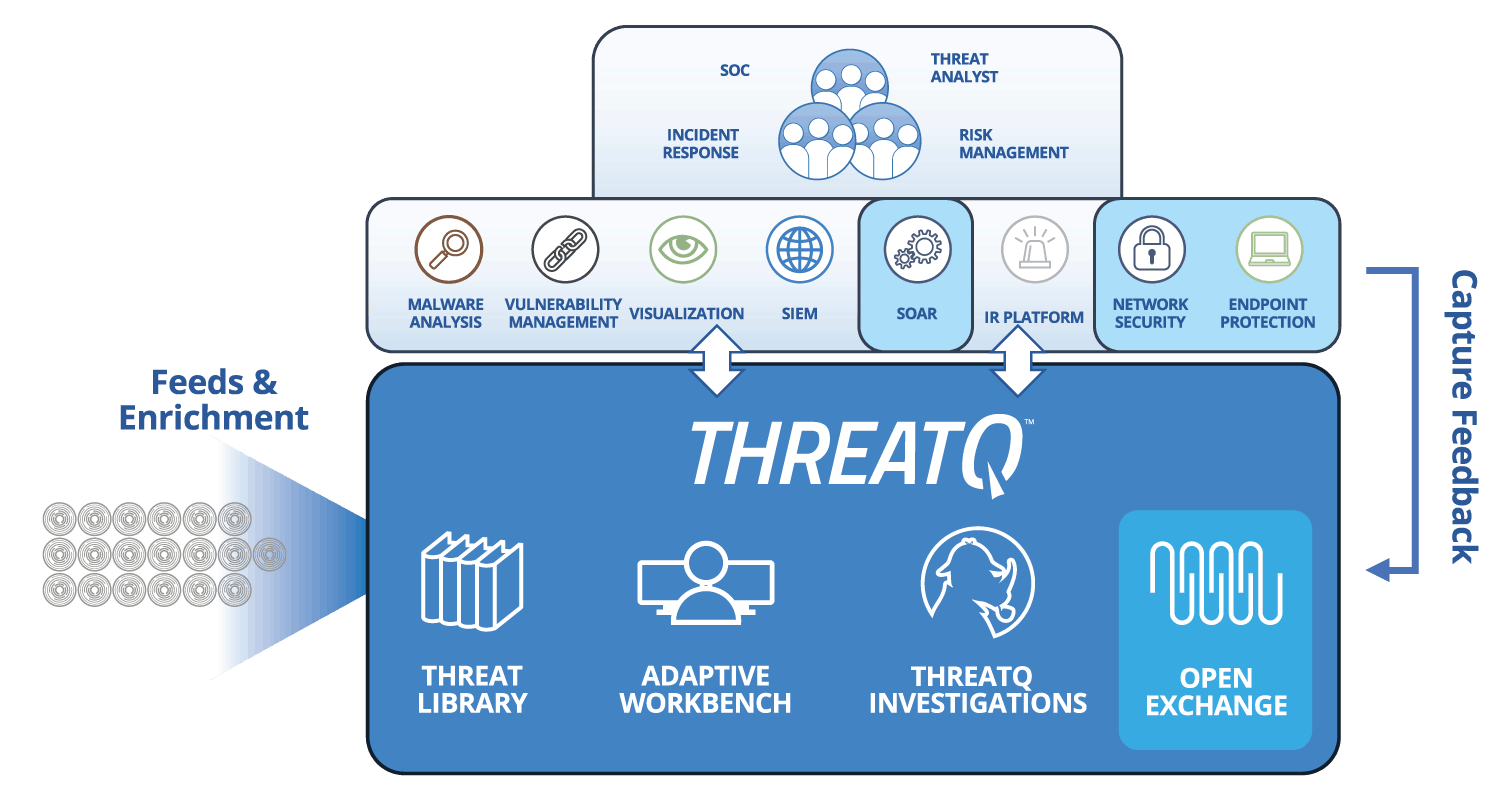
The ThreatQuotient data-driven threat intelligence platform helps to balance between human & machine focused approaches ensuring that teams always have the best tool for the job.
Learn more about ThreatQ TDR Orchestrator, the industry’s first solution to introduce a simplified, data-driven approach for no code/low code automation of spear phishing analysis resulting in more efficient and effective security operations.
How ThreatQ meets the spear phishing challenge
| 1 | Parse suspicious email |
|---|---|
| 2 | Added related indicators |
| 3 | Enrich data |
| 4 | Determine response |
| 5 | Automatically deploy indicators to security infrastructure |
| 6 | Assign tasks for response and mitigation |
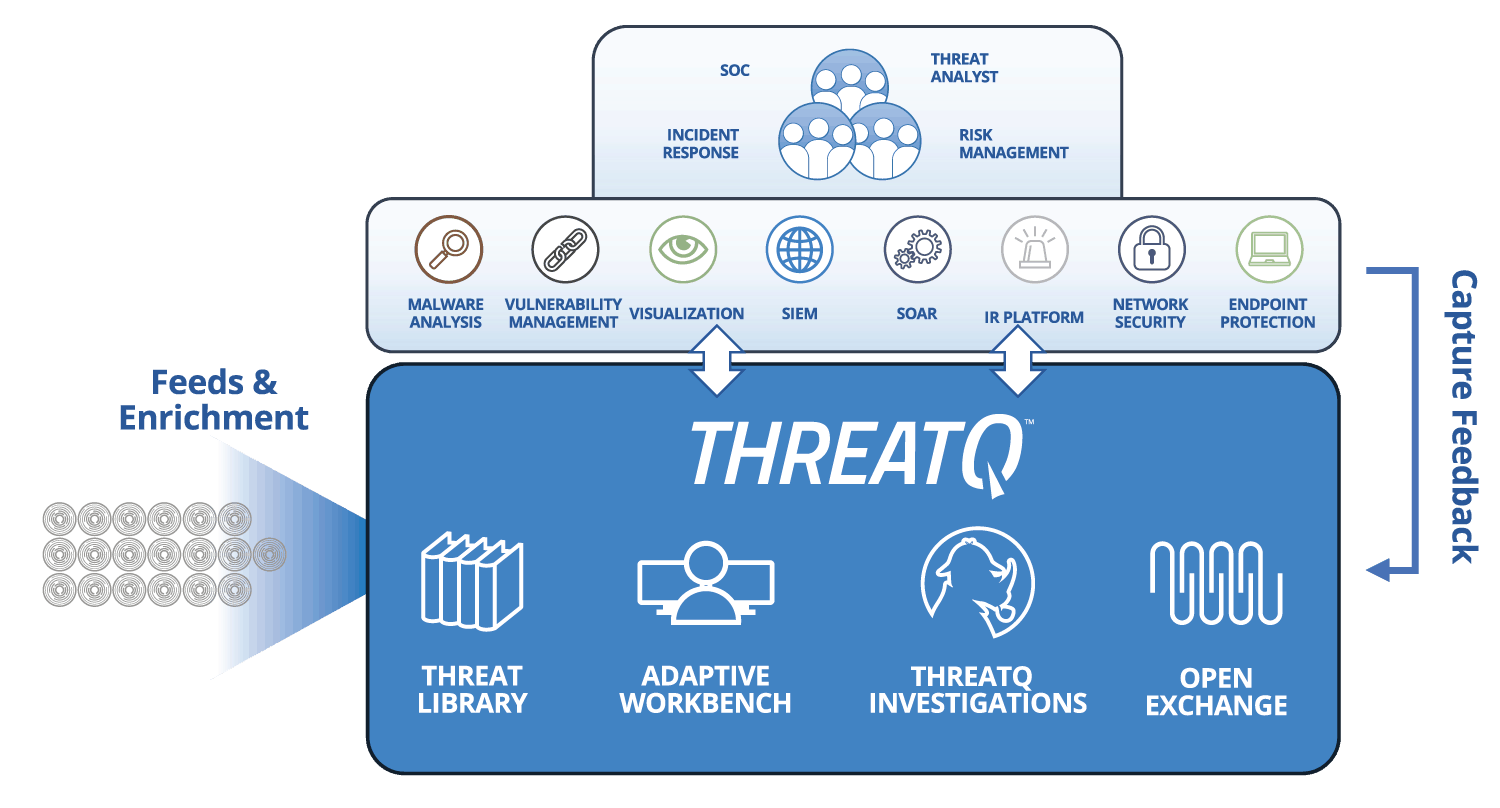
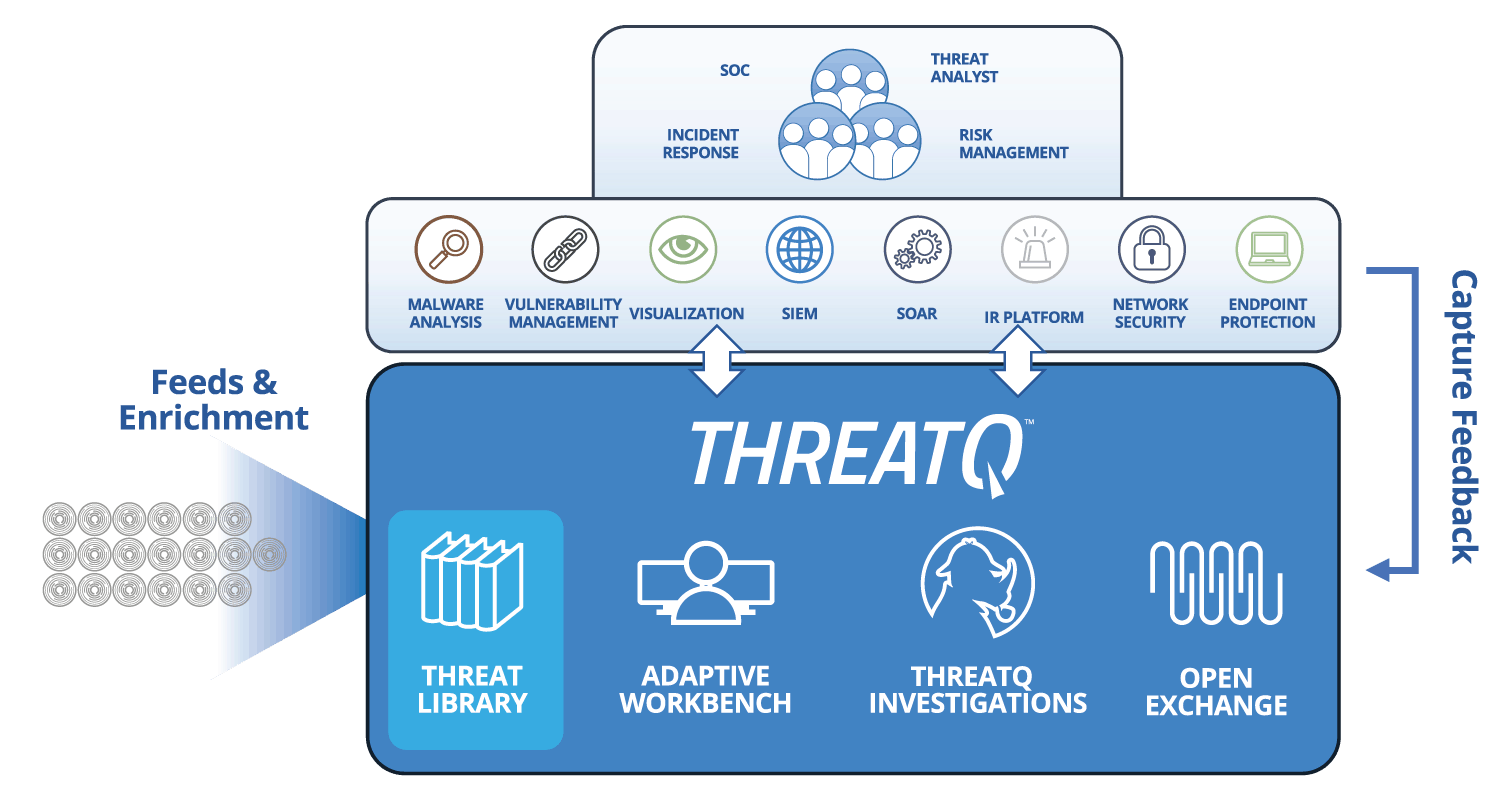
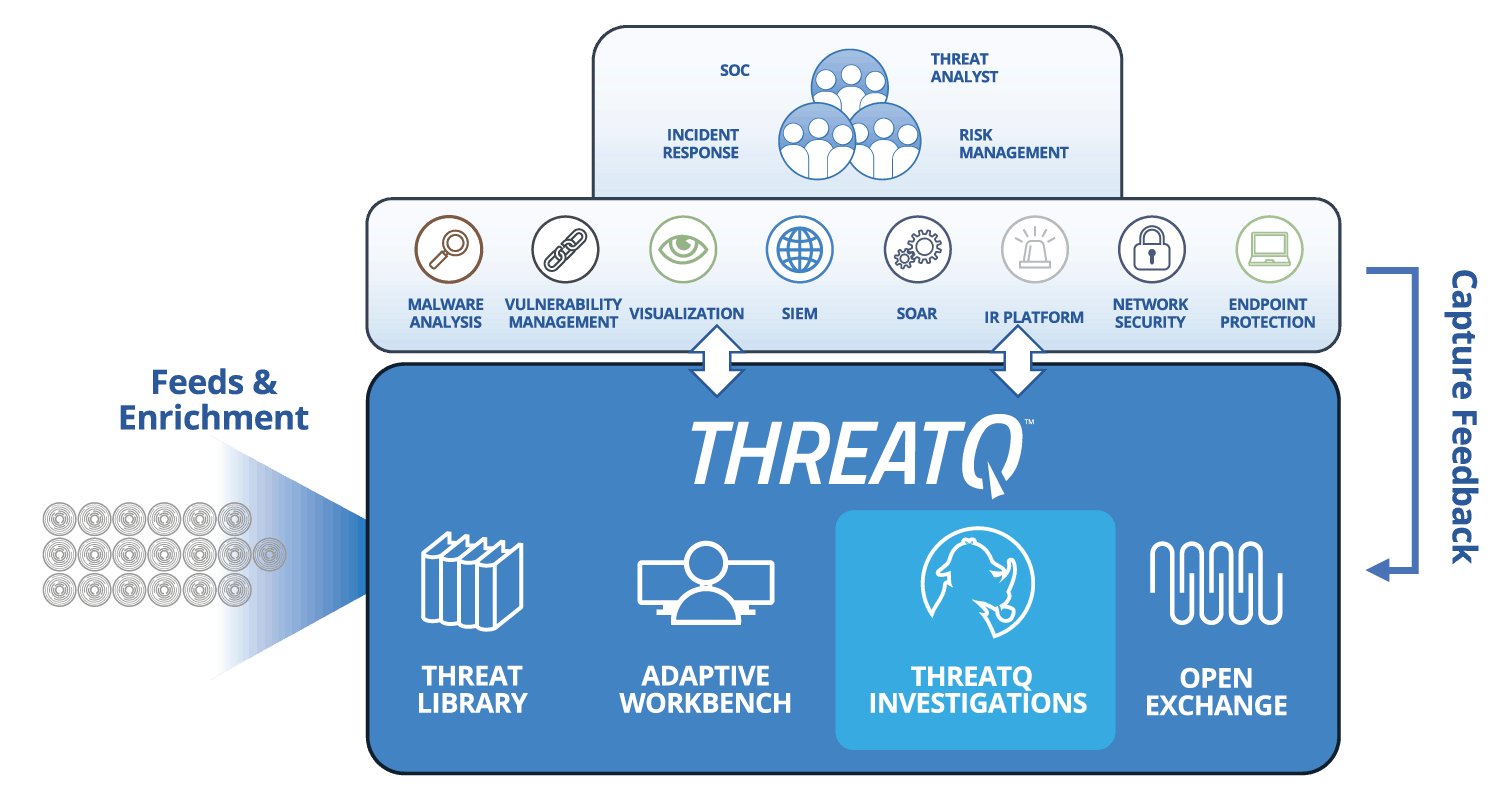


| Threat Library™ | Store global and local threat data in a central repository to provide relevant and contextual intelligence that is customized and prioritized for your unique environment. Learn More > |
|---|---|
| Customer-defined Scoring | Prioritize threat data automatically, understand why it is relevant and take action faster and with greater confidence. Lear More > |
| Spear Phish Parser | Automatically import and parse spear phish emails to identify threat data with intelligence value. |
| Events | Track and analyze events to assess their severity, relevance, and relationship to broader campaigns. |
Learn how to use ThreatQ
for spear phishing
Take a quick look at a spear phishing investigation using ThreatQ.
If you like what you see, schedule a demo for a deeper dive.
The ThreatQuotient approach to threat intelligence management
ThreatQ simplifies the process of parsing and analyzing spear phish emails for prevention and response. With a centralized Threat Library that aggregates all the external threat data organizations subscribe to along with internal threat and event data for context and relevance, analysts are in a position to begin to analyze and determine which emails to focus on.
Recipients of suspicious emails forward the email to an inbox that ThreatQ monitors continuously. Comparing indicators from the email against the data in the Threat Library, ThreatQ determines high risk emails versus low risk, allowing prioritization and noise reduction.
On high-priority items, ThreatQ automatically performs rear-view mirror searches on email logs using SMTP-specific IOCs – email subject, email sender, email filename/attachments. Analysts are able to identify spear phish attacks that might have fallen through the cracks because they were not identified as malicious at the time.
Going a step further, analysts can query to identify all the spear phish recipients and then overlap those findings with vulnerability scan results to determine the scope and help accelerate response and containment.
Outcomes:
- Triage spear phishing faster and more effectively based on analyst familiarity of adversary TTPs.
- Improved spear phishing attribution.
- Increased understanding of the environment and susceptibility to spear phish attacks.
- Proactive protection against spear phishing attacks.
LET’S GET STARTED!
Join the ThreatQ Community, a private community with hundreds of experienced cyber security pros sharing intel to level-up threat detection and response. Partner with ThreatQuotient to learn how we can help you focus on the threat.