
by Marc Solomon | Oct 3, 2023 | Blog
Unlocking the Power of Cybersecurity Automation: Insights from ThreatQuotient’s 2023 Research Marc Solomon Defined by relentless cyber threats and evolving challenges, the role of cybersecurity has never been more crucial. As organizations across the globe struggle...

by Noor Boulos | Sep 26, 2023 | Blog
What to Look for in a Security Operations Platform Noor Boulos Despite concerns of a global recession, a new IDC Worldwide Spending Guide forecasts cybersecurity investments will reach $219 billion in 2023, an increase of 12.1%. No doubt, the ongoing rise in...
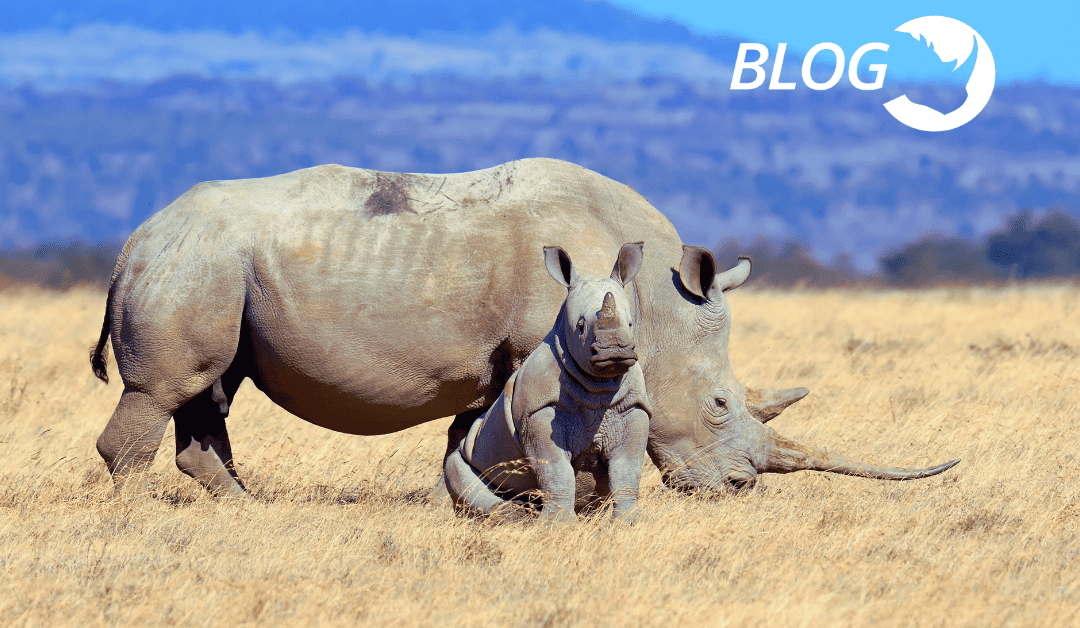
by Julia Weifenbach | Sep 19, 2023 | Blog, Corporate
Celebrating World Rhino Day 2023 Julia Weifenbach “ThreatQuotient’s love for the rhino can be felt in all aspects of our culture and company branding. Our commitment to rhino conservation is an integral part of our organization. World Rhino Day is an opportunity to...

by Haig Colter | Sep 12, 2023 | Blog
SecurityScorecard Integration with ThreatQ Enhances Your Visibility Into Your Critical Third Parties Haig Colter Third Party Risk as a Growing Problem With organizations becoming increasingly digitally connected, a lack of visibility into their vendors’ security...

by Leon Ward | Sep 5, 2023 | Blog
Synergizing Security: ThreatQ Investigations and ThreatQ TDR Orchestrator Leon Ward Organizations are continually searching for ways to strengthen their defenses against an ever-expanding array of cyber threats. One powerful strategy that has gained momentum in recent...

by Leon Ward | Aug 29, 2023 | Blog
Enhancing Cybersecurity with ThreatQ TDR Orchestrator: A Comprehensive Overview Leon Ward Organizations are constantly faced with an array of sophisticated cyberattacks that can compromise sensitive data, disrupt operations, and tarnish their reputation. To counter...







