If everything is important, nothing is. How to focus information to create actionable intelligence.
POSTED BY ROSS HAMMERThe high level of noise analysts face is a known fact. This is exacerbated when threat intelligence is entered directly into a SIEM or detection tools. Because all intelligence is seen as important, despite the availability of rating systems, information will trigger an alert that the analyst will need to either investigate or ignore if the volume becomes unwieldy. This “everything is important” approach overwhelms analysts.
I frequently demonstrate how ThreatQ can reduce the noise being brought in through threat feeds and alerts from systems. As I prepared for another demonstration, I spent some time fine-tuning the scoring on our ThreatQ platform and realized it would be a great way to explain how to focus information to create actionable intelligence.
To keep things simple for the demonstration, I selected 5 free feed sources to populate the system, along with reports on various threat actors and their associated information. One of my goals for the demonstration is to show how our scoring system is simple but highly configurable. For example, scores can be assigned for the source of the information, the type of data such as IP address, and if it has been associated with a threat actor.
As I was scoring and adding custom attribute scores, I noticed how easy it is to set a score too high on a single category or attribute, users should be aware that scoring in ThreatQ has many aspects. This is because the scoring system is compounded. If a high score is added to the source of information, and then a high score is added to the type of Indicator of Compromise (IoC), the indicator will appear to be important. This presents a problem. That score, based on two value points, may not be relevant to the organization, especially if it is from one source and has no additional context.
In the example below, there are nearly as many indicators considered “very high” as there are in all of the other levels combined. This definitely puts analysts on a path to becoming overwhelmed.
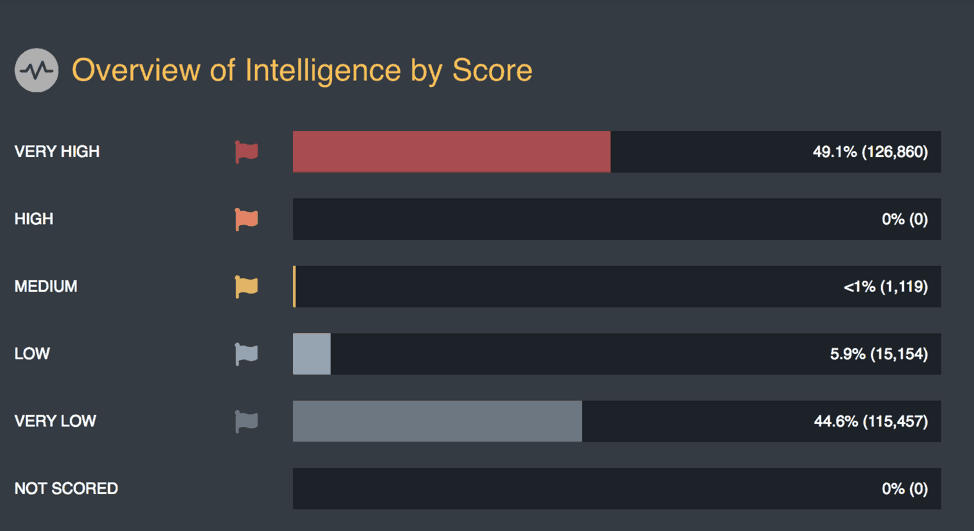
Figure 1: Overview of Intelligence Scoring in ThreatQ
For the critical IoCs to bubble up to the top, scoring should start low, allowing context and correlation to work. As an example, a feed that you trust and provides useful information and context should start as a 2.

Figure 2: Scoring Slider by Source
Types of IoCs that are important to the organization could also be set as a 2. Or using the Pyramid of Pain as a guideline, the following could be implemented: Hash Values at 1, IP Addresses at 2, and Domain Names at 3, as shown below.
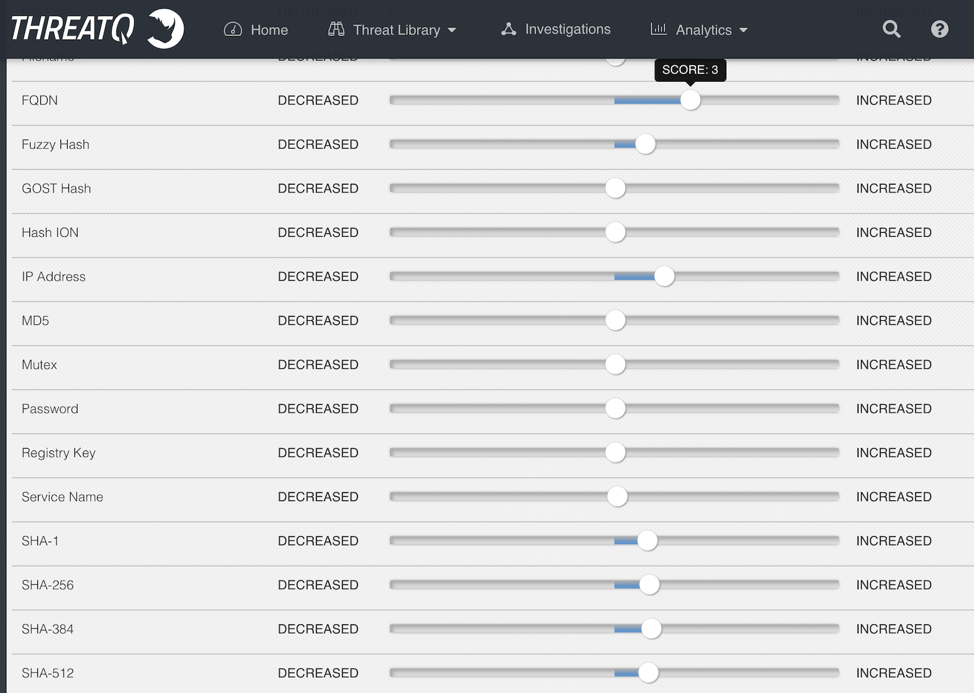
Figure 3: Scoring Slider by Indicator
Another example, within the IoCs are attributes that provide context to the IoC. Within the context there may be an attribute that provides a level of severity of the information — low, medium, or high. You can set a score for those attributes: 1 for low, 2 for medium, and 3 for high. In the example below, I will apply a score to the attribute Country. As I am concerned about IP addresses from China I will create a score of 3 based on the attribute.
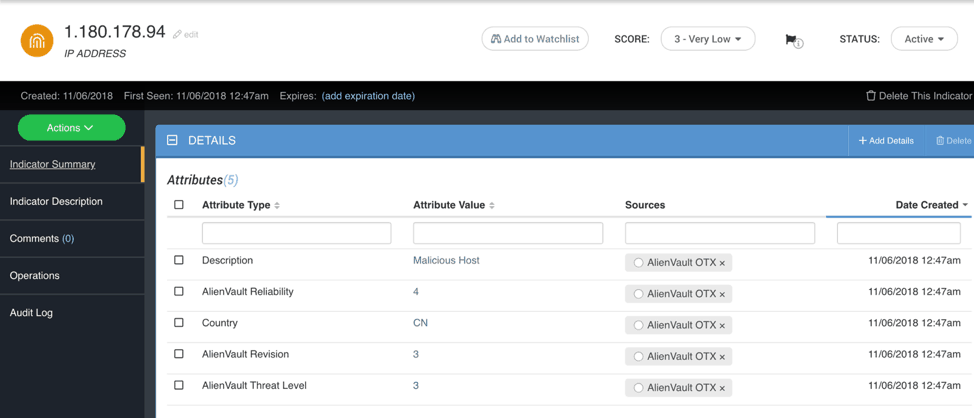
Figure 4: IP address details
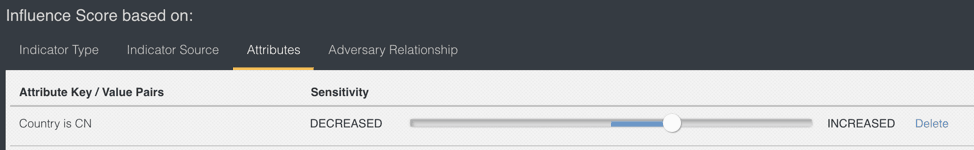
Figure 5: Attribute Scoring
At this point, the IoC has a compounded score of 7 (IP address = 2, Source = 2, Custom Attribute = 3) and is in the range of medium importance in our scoring system that goes from very low, low, medium, high, very high. The flag in the image below lists the criteria the indicator is being scored on.
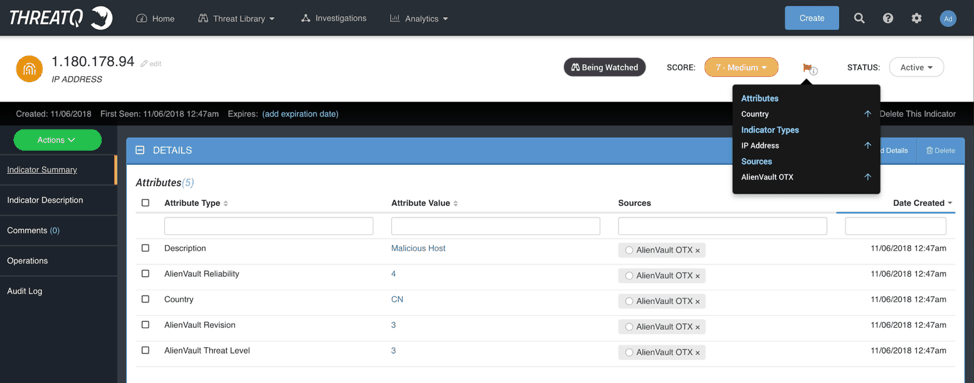
Figure 6: Indicator Scoring Criteria List
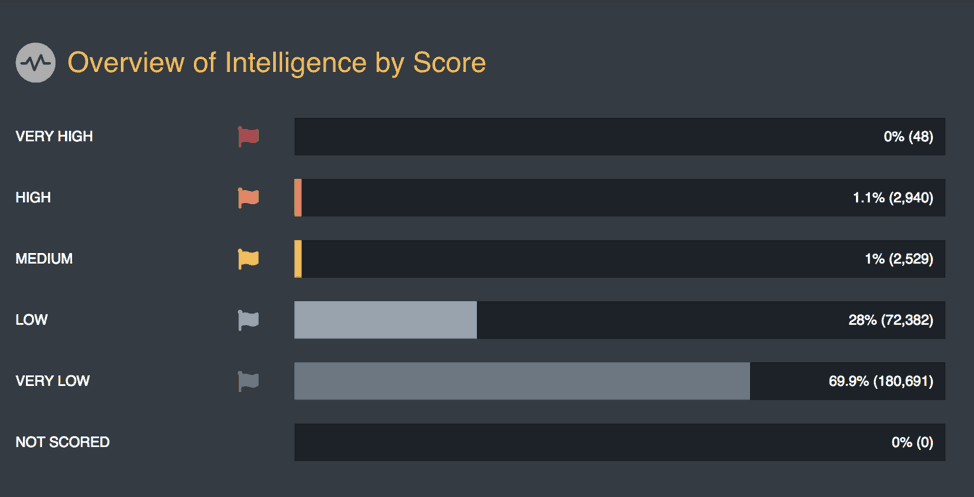
Figure 7: Overview of Intelligence Scoring in ThreatQ
What will elevate the IoC from a medium rating to high or very high is an additional feed source that reports the same IoC, or if the IoC was seen by one or more security tools integrated with ThreatQ. The inverse can be true as well, if an analyst has determined the IoC to be a false positive. Through a bi-directional integration with the tool the analyst is using and an attribute scoring policy set for false positives, the indicator score will be reduced. As shown below, the identification of the indicator as a false positive is reflected in the indicator’s attributes.
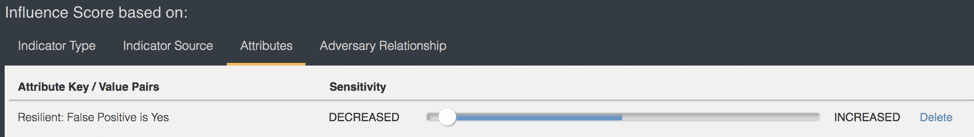
Figure 8: Negative Scoring in ThreatQ
Starting with a conservative approach to scoring allows the organization to see what is essential and adjust accordingly. Setting scores too high too soon can often be overwhelming, causing too many indicators to be pushed out, in this example to a SEIM. This isn’t to say there are not critical indicators, but fine-tuning and cross-checking through other sources validates the importance of each specific IoC to the organization.
In summary, there is a wealth of threat intelligence and information available to analysts that is broad and applies to many industries or teams in an organization. Determining what is relevant will reduce the noise and allow analysts to spend less time on lower priority information or false positives and more time on what is important.

0 Comments