USE CASE:
What is incident response?
Incident response is an organized approach to the process by which an organization handles the aftermath of a cyberattack or data breach with the goal of limiting damage and reducing recovery time and cost.
The challenge:
Once an event/alert is escalated to an incident, the investigation gains resources and visibility. Additional efforts need to be applied as quickly as possible to understand the scope, impact and the actions required to mitigate damage and recover. Gathering all the required information is a difficult and often manual process, and it comes in a great variety of formats from many different teams and tools.
If an incident under investigation can be related to a known campaign or adversary, the analysis and response time can be drastically reduced, since key tactics, techniques and procedures (TTPs) are already documented providing the proverbial breadcrumbs that lead to hiding places to look. Maintaining adversary profiles and historical incident response reports provides a jumpstart to any incident response investigation. But there is typically no central repository to store, share and update key learnings across teams, and no easy way to work collaboratively to accelerate investigation and response.
Learn how to use ThreatQ
for incident response
Take a quick look at how to use ThreatQ for incident response.
If you like what you see, schedule a demo for a deeper dive.
How ThreatQ meets the incident response challenge
| 1 | Create an investigation |
|---|---|
| 2 | Assess, research and assign tasks |
| 3 | Complete tasks and publish findings |
| 4 | Determine response |
| 5 | Store learnings to increase organizational memory |

| Customer-defined Scoring | Prioritize threat data automatically, understand why it is relevant and take action faster and with greater confidence. Learn more > |
|---|---|
| Open Exchange™ | Integrate ThreatQ with existing security tools, teams and workflows through standard interfaces to extend their value, knowledge and efficacy. Learn more > |
| Threat Library™ Search | Quickly research and understand context behind possible threats by keyword, attribute and object name. Group and pivot on associated data and quickly take bulk actions across a full group of data. Learn more > |
| Watchlist | Add specific IoCs, adversaries or other threat related data to your dashboard to highlight changes. |
| Collaboration | Share indicators, relevant data, events and incidents with different members of the team automatically and simultaneously as well as external parties through reporting and export capabilities. Learn more > |
| Timelines | Document a chronological record of an incident automatically, and relate it to key events and breach artifacts. Watch the video> |
| Tasking | Collaborate and coordinate response and investigations between members of cross functional teams. |
| Reporting | Build strategic, operational and tactical reports including those for malware, campaigns, and adversaries.to share with other teams, management or clients. |
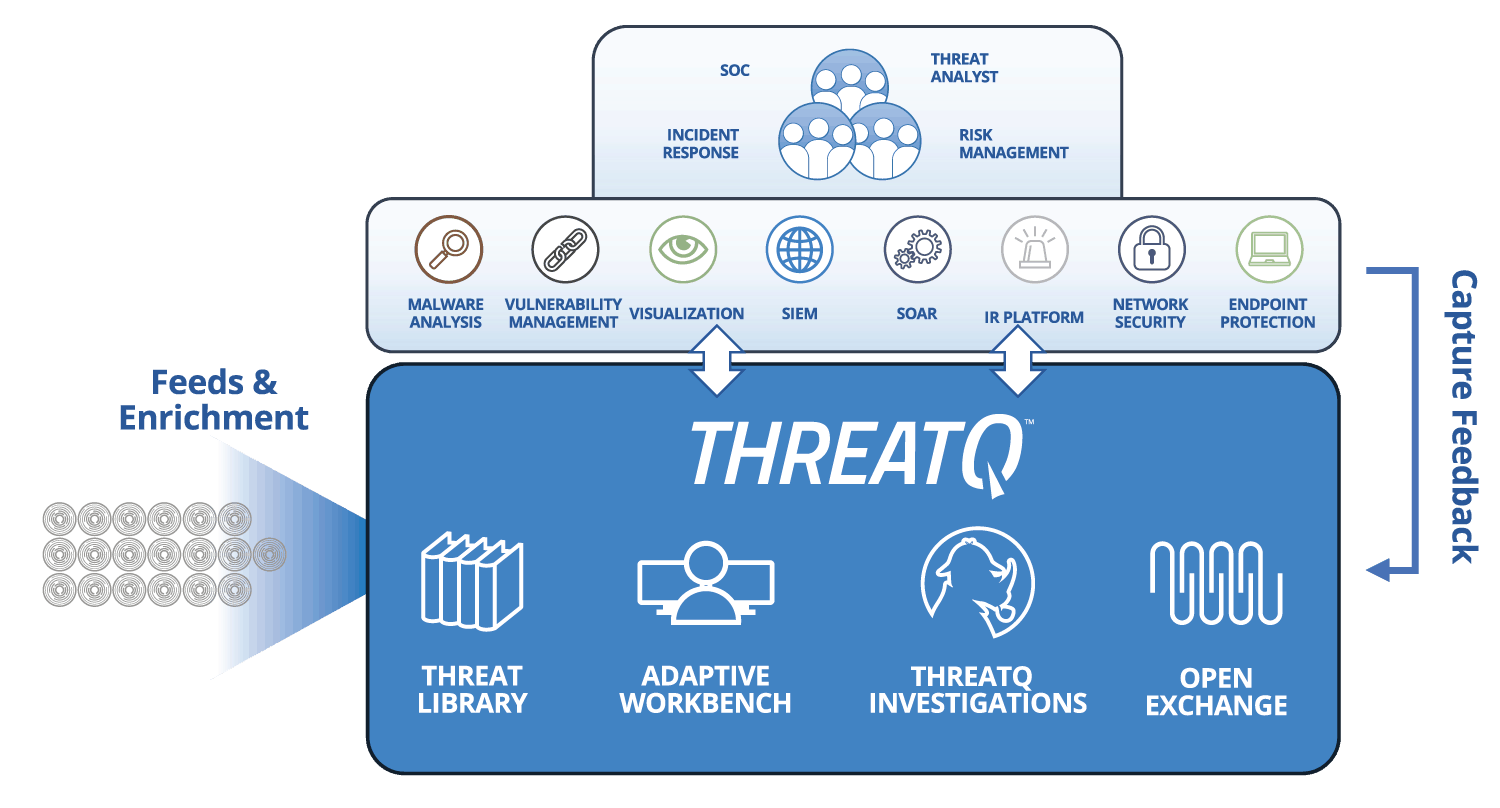
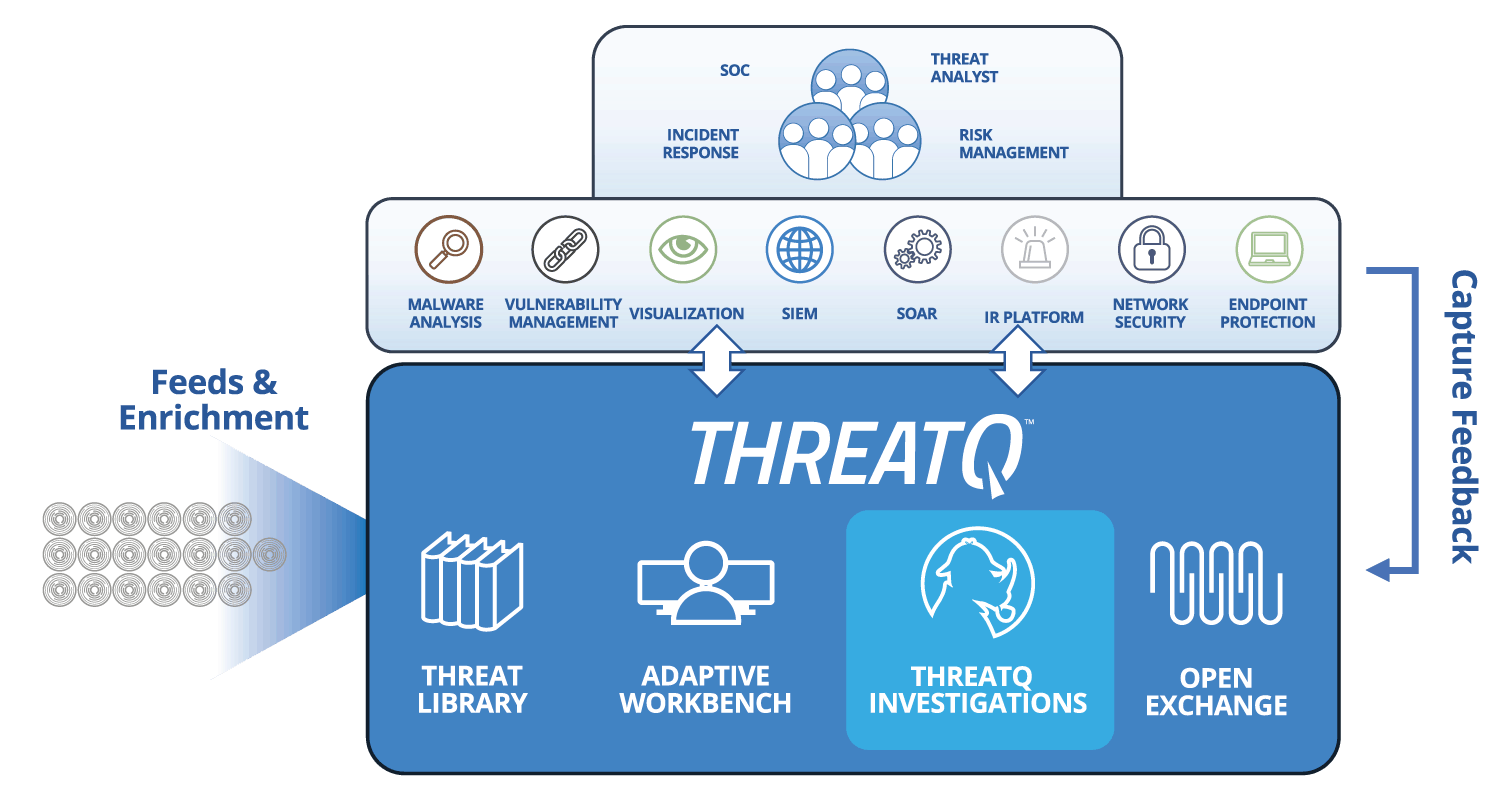
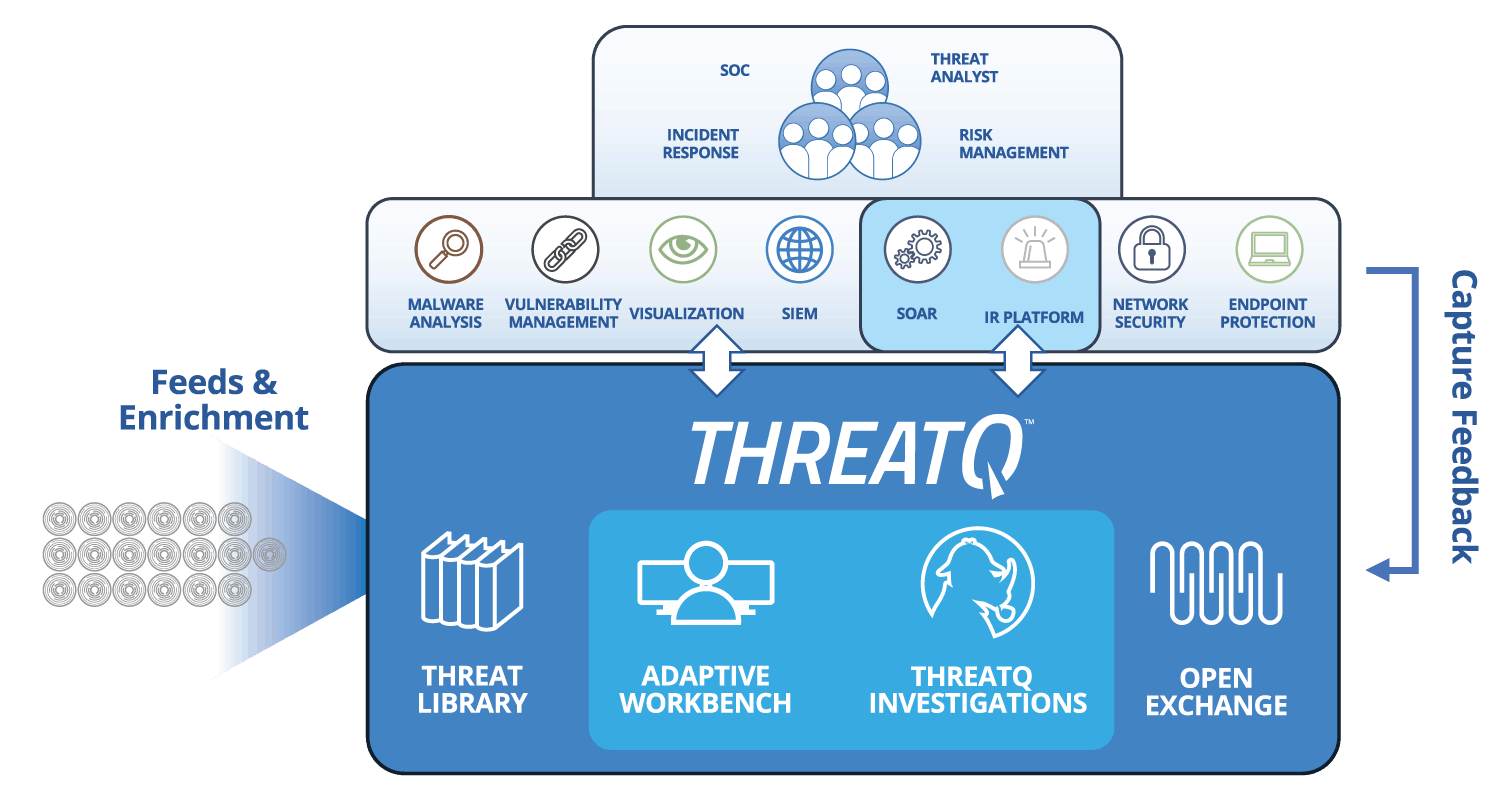
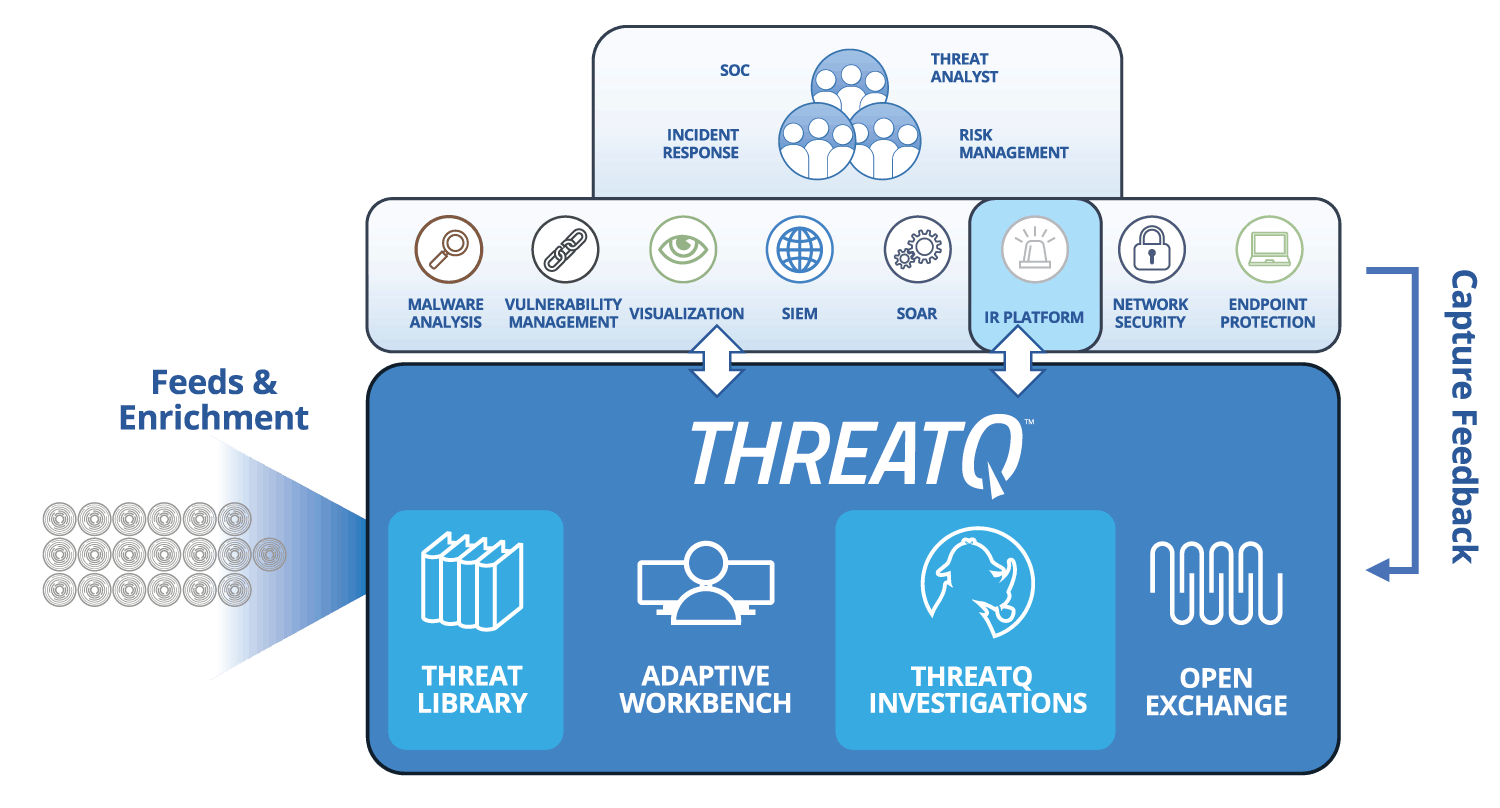
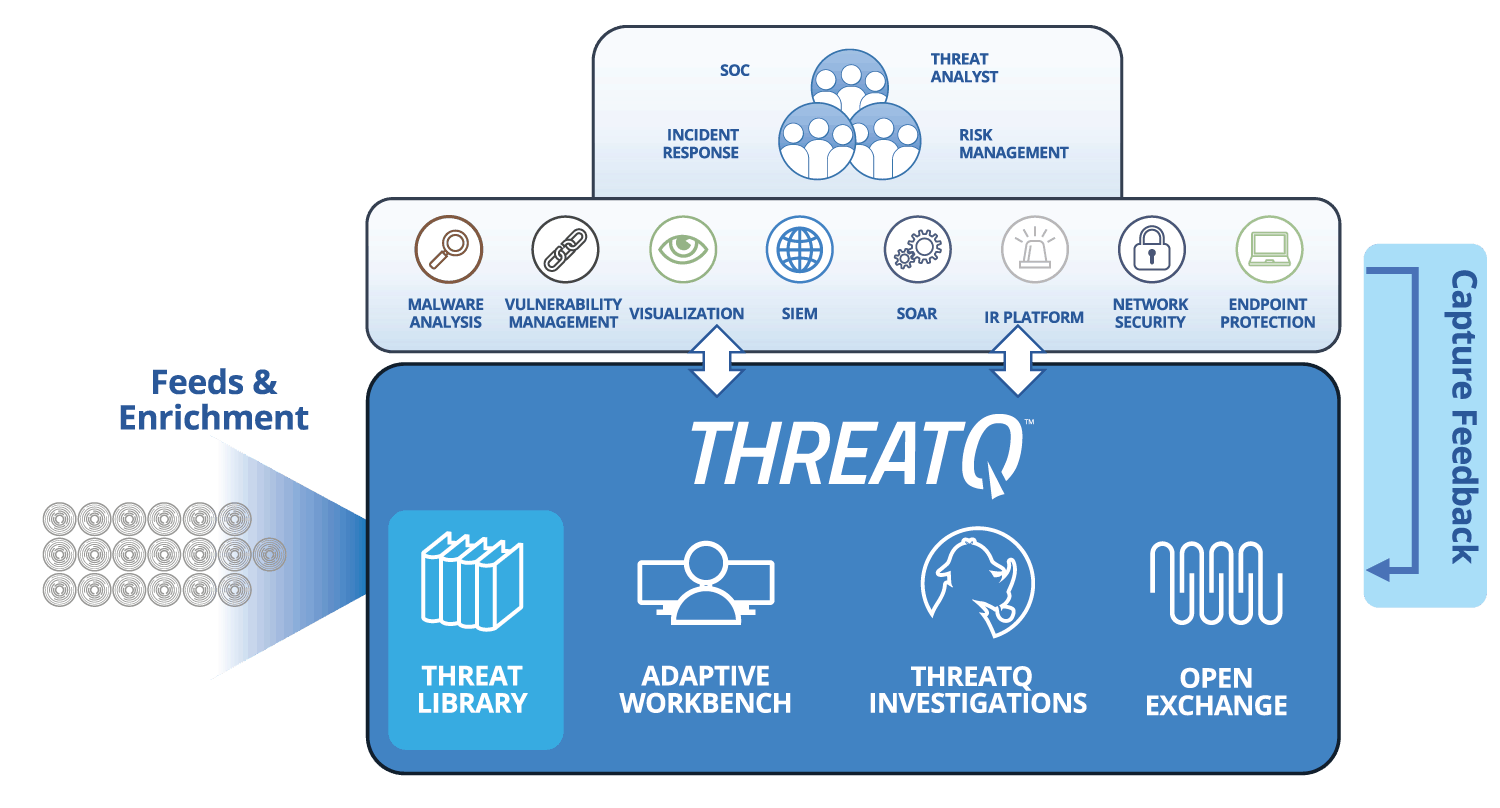
The ThreatQuotient approach to incident response
ThreatQ and ThreatQ Investigations are designed to support the fact that incident response is a team sport. Start by importing an event/investigation along with any peripheral intelligence into a shared investigation environment. This instantly allows an incident responder to quickly assess what other research has been performed and by whom, what tasks need to be assigned, and how all the data relates. The ability to include the necessary resources from outside the immediate security department (i.e., database administrators, application specialists, etc.) ensures complete situational understanding and engages the full set of capabilities of the organization. As the necessary responders from around the organization complete tasks and publish them to the larger incident canvas, the team progresses towards identifying patient-0 and re-arming the organization against the next wave of attacks.
If a team knows their attackers’ tactics, techniques and procedures (TTPs) , then as that intelligence comes in, they can be scored appropriately and even be added to a “watchlist” for visibility. This is a subtle and proactive way to keep a finger on the pulse of malicious activity. When adversary profiles are frequently updated and maintained with the latest attributes, new analysts can learn about the adversary exponentially faster.
IR teams tend to work within specialized IR platforms. A two-way integration with a threat intelligence platform ensures that the user can focus on their processes and procedures without the need to switch back and forth between multiple interfaces and platforms.
Documenting investigations that can be correlated to future cases, results in organizational memory and ability to correlate investigations that may have seemed to be separate, but are in fact part of a single campaign.
Outcomes:
- Better analysis is performed.
- Faster response time and time to resolution.
- More incidents can be completed.
- Current incident resolution is faster by applying past learnings.
- Better team collaboration and productivity.
- Increased new hire ‘time-to-value’ (TTV).
- Faster and more complete understanding of how to orchestrate a coordinated response.
LET’S GET STARTED!
Join the ThreatQ Community, a private community with hundreds of experienced cyber security pros sharing intel to level-up threat detection and response. Partner with ThreatQuotient to learn how we can help you focus on the threat.
