Intelligent Consolidation Rules All - the Underbelly of Communities
POSTED BY RYAN TROSTAs an analyst you are always subconsciously consolidating information looking for investigation patterns, trends, or even the slightest hint of an attacker bending RFC rules to their advantage. I was recently catching up with a friend and he mentioned the pain points involved in trying to consolidate indicators and contextual data across a competitor’s platform due to their multiple communities. He needed threat intelligence management capabilities that could cater to his highly federated environment because they have to deal with competing sub-organizations, government data with restrictive TLP, and tight-lipped industry data. The considerable time, effort and cost he had to expend consolidating information, highlights the underbelly of non-consolidation in a platform.
ThreatQ’s Threat Library provides threat intelligence management capabilities that consolidate intelligence by object – indicator, event, adversary, etc. The easiest way to demonstrate this is to show you the Indicator Detail page. This initial view provides a quick litmus test including – score, status, watchlist, created date/first seen date/ expiration date, # of attributes, # of sources, # of related files/events/indicators, etc. At the very least, as an analyst this gives me a pretty good sense of how devious this indicator is.
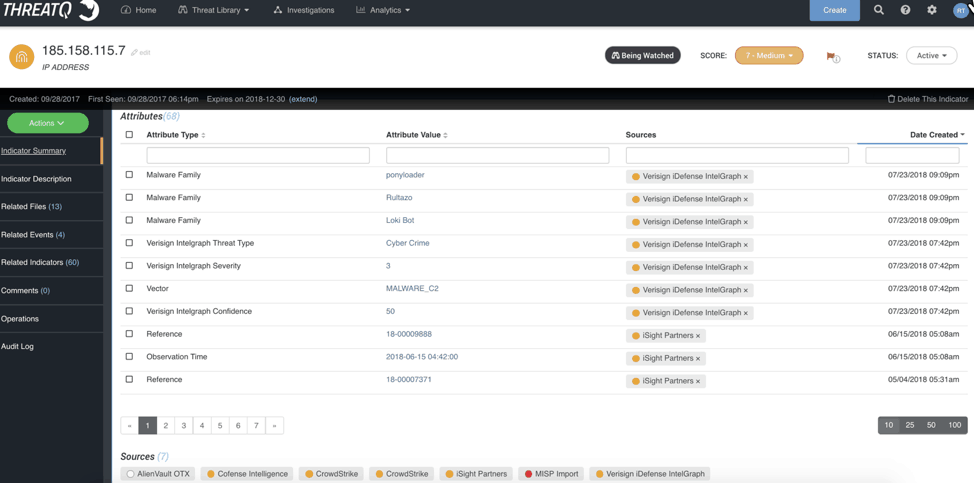
Figure 1 – Indicator Detail page shows how threat intelligence management consolidates the information within the platform
So, what do I mean about “intelligent consolidation”? There are two intelligent consolidations to highlight on this page. The first element to highlight is the collection of Sources. You’ll notice there are six unique Sources and seven entries – CrowdStrike is duplicated because it released the indicator in separate reports roughly two weeks apart. A user can immediately hover over each Source to view the basics – TLP and Date Published.
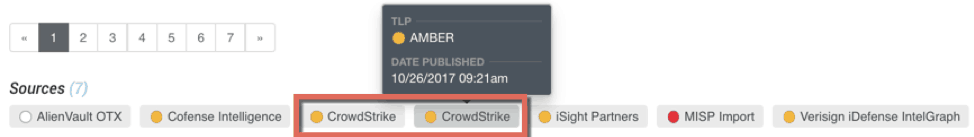
Figure 2 – Highlights the intelligent consolidation of Sources
The second intelligent consolidation is how the Threat Library matches up identical attributes and groups them together, as shown in Figure 3. In this example you will see that Cofense, CrowdStrike, iSight Partners, and Verisign iDefense have all published this IP address associated with the Malware Family Trickbot. Identical to the Source hover, an analyst can hover over each Source to show the TLP and Date Published date. This consolidation is paramount to expedite an investigation, research effort, or even a hunt because the analyst doesn’t have to scour the 68 other attributes provided by the commercial services and perform the mental acrobatics necessary to tie them together as you do in other platforms that don’t exhibit the same intelligent consolidation.
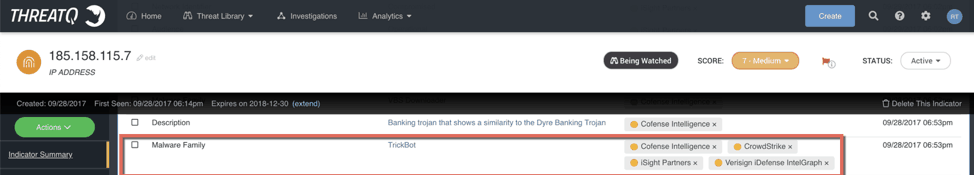
Figure 3 – Demonstrates the intelligent consolidation of Malware Family across four Sources
What does this look like in systems from other vendors? It is painful to say the least. The single IP address either has an entry per community or, even worse, an entry per source, resulting in seven individual records of the same IP address. The mental acrobatics necessary to subconsciously consolidate the indicator’s data is hard enough but, to make matters worse, the community architecture means you don’t have a central repository to deploy the best dataset of intelligence to your sensor grid. Rather, you must manually consolidate the data from secondary communities into your primary community before deploying OR you can deploy the most malicious intelligence from each community, but as competitors are pay-per-API that gets expensive quickly.
Fortunately, you have an alternative approach with ThreatQ’s threat intelligence management capabilities that do this legwork for you with no add-on fees.

0 Comments