The Meaning of Orchestration
Vicki LemayThe intent behind SOAR, and orchestration in general, has never been to increase the workload of an already stressed department, but to ease the burden of rote manual tasks required to investigate and mitigate a threat. However, getting to this state means taking a step back and reevaluating where automated tasks are most valuable – and for an organization that’s thinking about incorporating orchestration into their system, the following steps are a good place to start:
- Defining the mission of the organization’s security operations team
- Outlining the processes that can and/or should be automated to achieve that mission
- Leveraging the toolset that compliments the skills map of the team to bring the plan to fruition
Diving straight into the second step (every team’s mission is going to be different) – during the forum we also asked customers what functions are the most important to automate. They responded with detection as the prime candidate, which immediately raised the question of how do you scale detection automation without drowning your analysts in alerts? Here is where ThreatQ TDR Orchestrator can help. ThreatQ TDR Orchestrator is built off of a feature that veteran ThreatQuotient customers are already familiar with – the Threat Library.
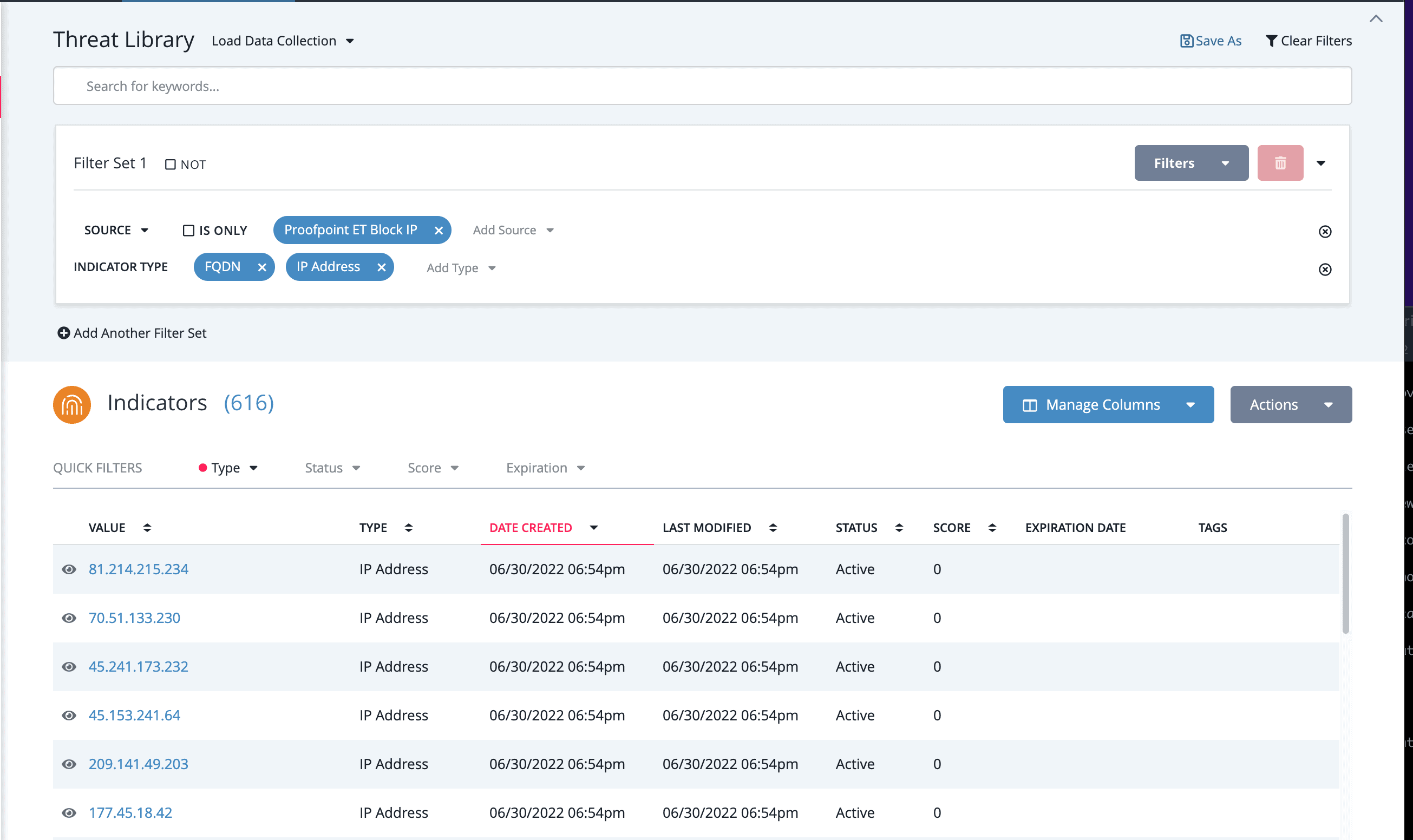
Using Smart CollectionsTM, which are custom built by analysts with filters relevant to a particular organization’s priorities, the data input into an automated process (what we call a Workflow in ThreatQ TDR Orchestrator) can be limited to just the necessities so that analysts have more control in ensuring that alerts are meaningful. And there are additional benefits to structuring data inputs this way. Smart Collections (and by extension Workflows) are set-and-forget – when a Workflow is triggered, a realtime search is kicked off using the saved filters, meaning the result set is always up to date with the system library. More importantly, using a Smart Collection reduces human error by eliminating copy and paste mistakes at scale. And since the Workflow is already operating within a threat intelligence platform, existing rules around managing duplicate entries and audit log tracking are automatically applied to any enrichment actions.
Building a Workflow in the ThreatQ Platform involves three steps:
- Choosing a Smart Collection to use as an input data set
- Defining a cadence for when the Workflow should run, and
- Adding Actions – the tasks to be automated for the input data set
All three of these steps can be completed in the UI, with the resulting Workflow visualized in a clickable node graph.
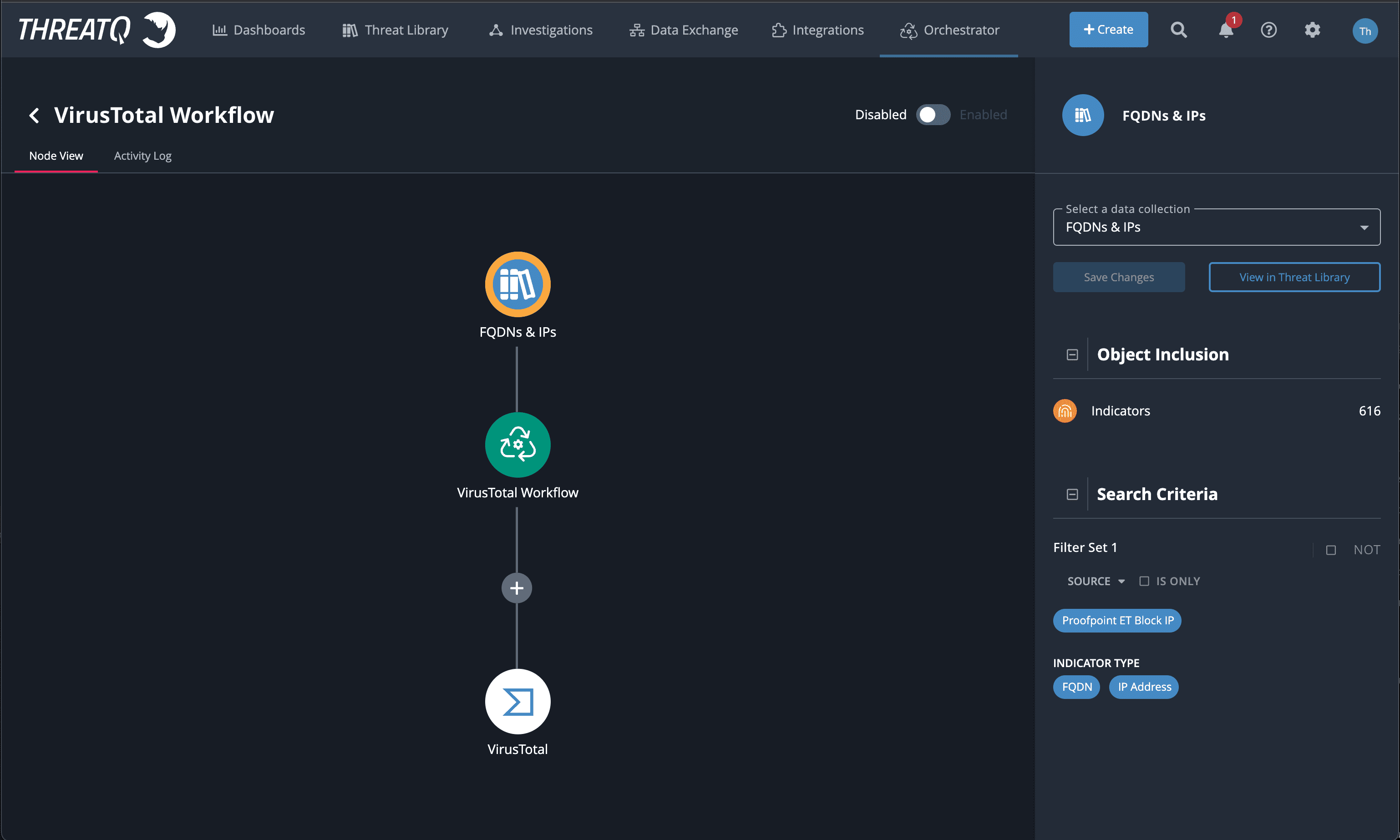
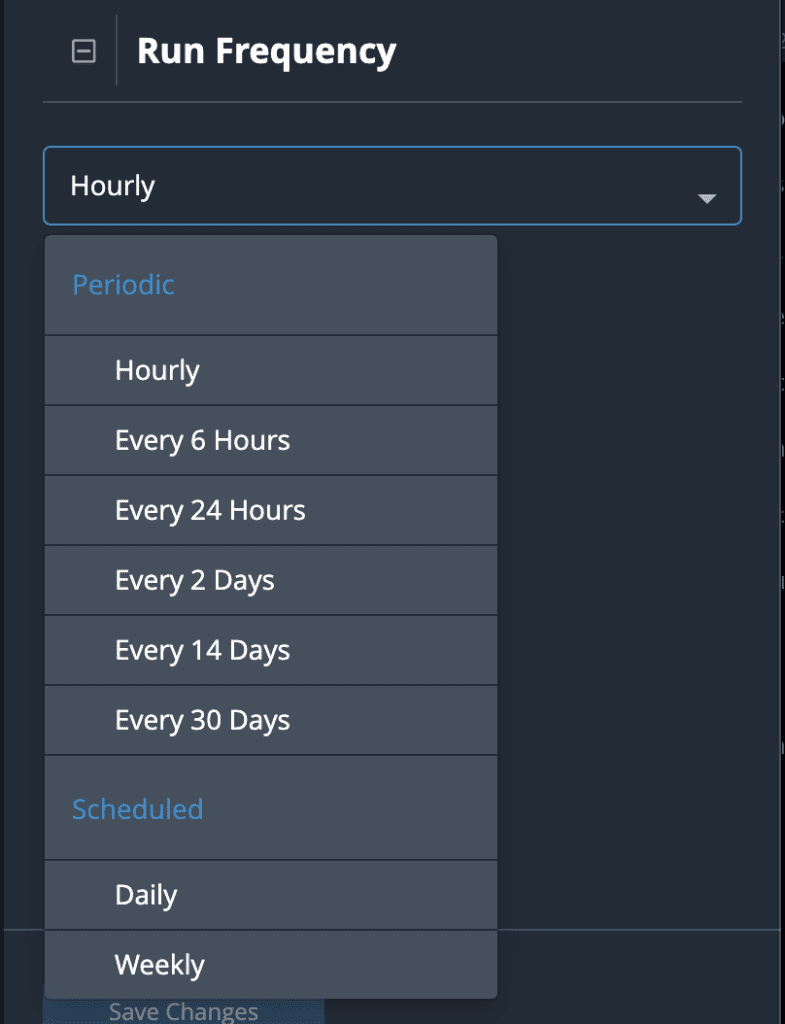
Configuration is managed on a per-node basis, making parameters easy to set, review, and update. Actions can be added and removed as needed and Smart Collections can be altered without having to start from scratch. And when it comes to determining how often a Workflow should be run, with ThreatQ TDR Orchestrator a new range of more granular frequencies has been introduced – including both periodic (daily, monthly) and scheduled (daily at a specified time) options. In this way Workflow runs can be tailored to accommodate query limits for any Actions that involve polling.
Implementing an effective orchestration strategy doesn’t have to be complicated. Our goal with ThreatQ TDR Orchestrator is to take the onus of setup and configuration off of analysts so that they can focus on what they want to do (security). Simplifying automation down to running a curated data set against the integrations that matter most to a team is a good place to start.
To learn more about orchestrator and cybersecurity automation adoption visit here: https://www.threatq.com/threatq-tdr-orchestrator-resources/

0 Comments