The ThreatQuotient Blog
EXPERTS SHARING THEIR CYBER THREAT INTELLIGENCE INSIGHTS AND EXPERIENCESBlog I Don’t Take the Bait: Recognize and Report Phishing Attempts
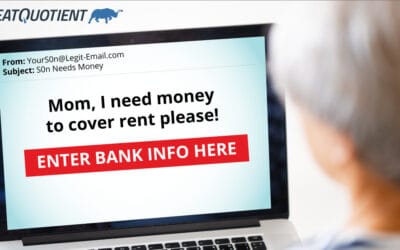
Phishing attacks, which involve fraudulent attempts to trick individuals into divulging sensitive personal information, remain a significant threat. Despite advances in cybersecurity, hackers continue to…
Blog I Keep Your Software Update Routine Strong
Software is an essential part of our online experience. Whether it’s our operating systems, web browsers, or the apps we use daily, software plays a crucial role in our lives. However, with great convenience…
Blog I Strengthening Cybersecurity: The Importance of Multi-Factor Authentication
Safeguarding your own personal digital ecosystem is your responsibility. However, the effectiveness of your organization’s cybersecurity measures heavily relies on the collective efforts…
Blog I Fortify Your Security with Passwords and Password Managers
The internet has become an integral part of our daily lives, protecting our online accounts and sensitive information is more critical than ever. Passwords are the first line of defense against cyberattacks, and…
Blog I Stay Secure: Your Guide to Cybersecurity Awareness Month 2023
October has arrived, and with it comes one of the most crucial awareness campaigns in the digital age: Cybersecurity Awareness Month (CSAM). As we navigate an ever-changing and technologically advanced…
Blog I Unlocking the Power of Cybersecurity Automation: Insights from ThreatQuotient’s 2023 Research
Defined by relentless cyber threats and evolving challenges, the role of cybersecurity has never been more crucial. As organizations across the globe struggle with the ever-expanding threat…
Blog I What to Look for in a Security Operations Platform
Despite concerns of a global recession, a new IDC Worldwide Spending Guide forecasts cybersecurity investments will reach $219 billion in 2023, an increase of 12.1%.
Celebrating World Rhino Day 2023
For five consecutive years, ThreatQuotient has proudly embraced World Rhino Day on September 22nd as an opportunity to spotlight the extraordinary efforts of Helping Rhinos in safeguarding rhinoceros populations…
SecurityScorecard Integration with ThreatQ Enhances Your Visibility Into Your Critical Third Parties
With organizations becoming increasingly digitally connected, a lack of visibility into their vendors’ security diligence has made exploiting these relationships a go-to tactic for…
Synergizing Security: ThreatQ Investigations and ThreatQ TDR Orchestrator
Organizations are continually searching for ways to strengthen their defenses against an ever-expanding array of cyber threats. One powerful strategy that has gained momentum in recent…
Enhancing Cybersecurity with ThreatQ TDR Orchestrator: A Comprehensive Overview
Organizations are constantly faced with an array of sophisticated cyberattacks that can compromise sensitive data, disrupt operations, and tarnish their reputation. To counter these…
Maximizing Efficiency and Effectiveness with ThreatQ Investigations
Organizations in all industries are facing an ever-increasing number of cyber threats. To combat these threats, security teams need to be equipped with powerful tools and technologies…
Expert Advice on Prioritizing, Automating and Collaborating for Threat Detection and Response
In a recent panel discussion led by David Neuman, Sr. Analyst with TAG Cyber, ThreatQuotient’s Dave Krasik, Sr. Director of Product Management and Jessica Bair…
Enhance Threat Detection and Response with Intel DNS
ThreatQuotient and Infoblox recently hosted a webinar, where they demonstrated how the combination of DNS Intel and the use of a Threat Intelligence Platform (TIP) help to improve threat detection and response capabilities.
Using Threat Hunting to Uncover Cybersecurity Threats
In the fast-evolving digital landscape, the prevalence of cyber threats has become a stark reality for businesses and individuals alike. The conventional cybersecurity measures, while essential, are often reactive and inadequate…
Enhancing the Capabilities of National Cyber Agencies
In today’s interconnected digital landscape, cyber threats have become more and more sophisticated and prevalent, posing a huge risk to individuals, organizations, and even nations.
ThreatQ Cyber Forum Recap: Expert Insights on Risk-Based Vulnerability Management
The discipline of vulnerability management has been around for decades and the way we assess risk, based on severity and likelihood of exploitation, has remained fairly constant.
4 Steps to a Comprehensive Security Approach
Software supply chain attacks have become a major concern for organizations in recent years, as cybercriminals increasingly target third-party software components and libraries used to build applications.