Using ThreatQ and Blueliv to Gain Greater Insights and Prioritize Threats
In this day and age, almost every device is a potential target for some form of malicious attack. In this post, we will take a look at the intelligence that Blueliv Threat Intelligence Feed provides in order to help combat these attacks. Blueliv provides detailed information on compromised URLs, domains, and IPs, as well as crime servers, botnets, and additional information on attacks and malicious files.
One of the first steps is to bring intelligence from Blueliv into the ThreatQ threat intelligence platform. Using the documentation found here, we are able to easily integrate Blueliv’s intelligence into the ThreatQ Threat Library.
Using the ThreatQ scoring, you can also score and prioritize based on the Blueliv source, attributes, and indicator types. Individual indicators may be manually scored as well. This scoring algorithm will help you to better comprehend and fit the data to your organization’s needs. This can be seen in Figure 1 and Figure 2 below.
 Figure 1: Scoring an individual indicator
Figure 1: Scoring an individual indicator
 Figure 2: Using the ThreatQ Scoring System to score the Blueliv source
Figure 2: Using the ThreatQ Scoring System to score the Blueliv source
The Blueliv feeds for crime servers and malware also provide their own ‘scoring’ system via their attribute, ‘Confidence’. For IPs, FQDNs, and URLs, this score can be a number 0 through 5, with 5 being high risk and 0 being low risk. For malware, this score is either low, medium, or high. Paired with ThreatQ’s scoring, these feeds can be filtered and exported with even more accuracy to your organization’s needs.
By default, the integration fetches from all four of Blueliv’s feeds (malware, botnets, attacks, and crime servers), however, this can be configured to your needs. You can choose a single feed, multiple feeds, or all of the feeds.
Once the indicators are in the ThreatQ threat intelligence platform, you will be able to view the data by searching by source or by a certain attribute. The ThreatQ threat intelligence platform also makes it easy to find indicators that have overlapping information from different sources. For instance, I can search for a malicious domain from the Blueliv source, and find indicators that have been picked up by other sources. In Figure 3 below, you can see that this FQDN has been picked up by Blueliv as well as by the abuse.sh ZeuS Block FQDN open source feed.
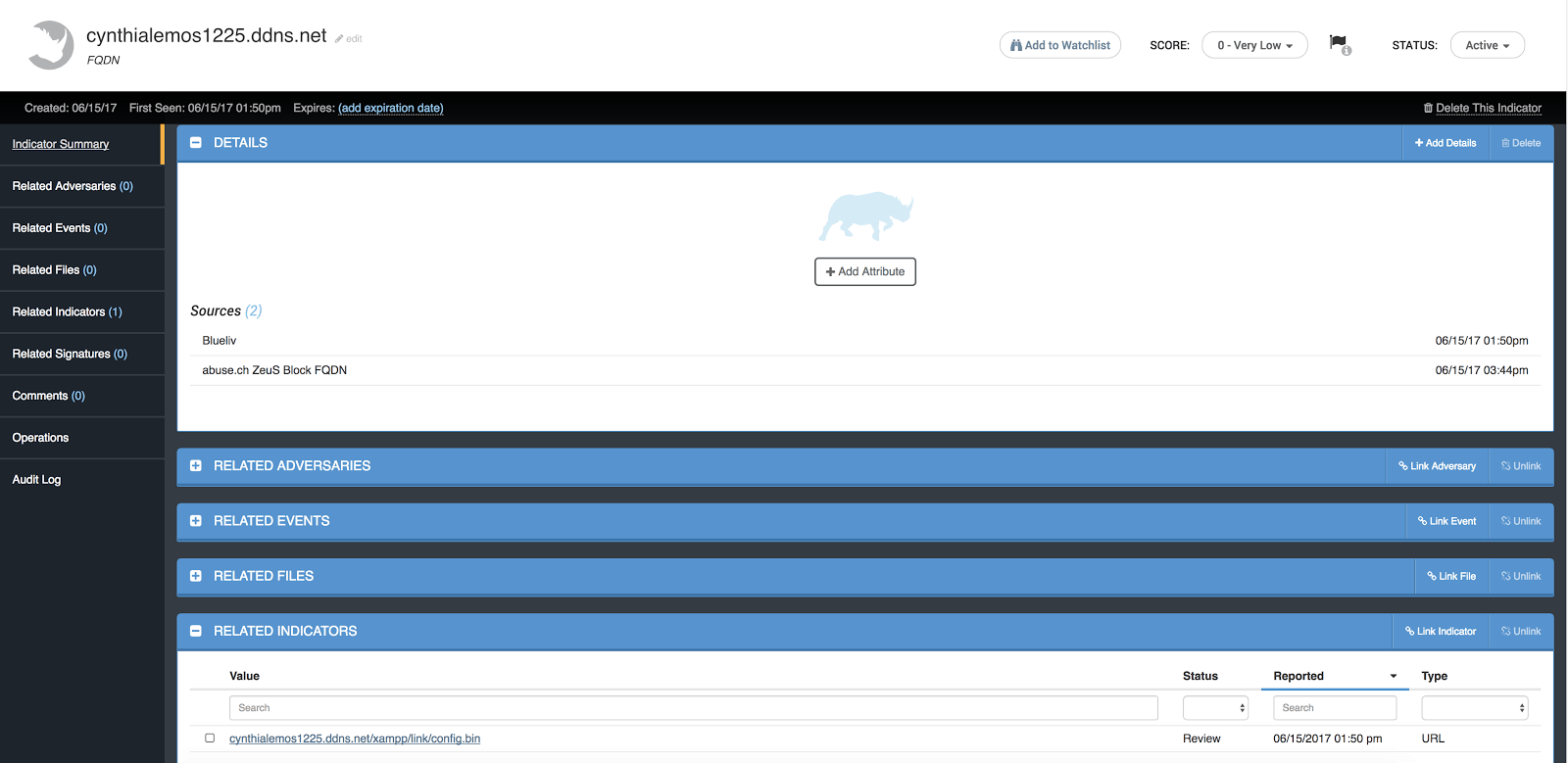 Figure 3: Viewing an indicator with a related indicator
Figure 3: Viewing an indicator with a related indicator
This FQDN does not have any attributes associated with it. However, if you look at the related indicators section, you will see that there is a related URL. Pivoting to the entry will take you to more details that Blueliv has about that URL (and FQDN) as seen in Figure 4. We can see that the URL was used for the trojan horse, Citadel, and is also used for Command and Control. Additionally, we can see that Blueliv gives it a confidence level of a 4 (scale 0-5) which, when paired with ThreatQ’s scoring, suggests it might be considered higher priority. We can even dig a little deeper by clicking to bring up a search for the attribute value.
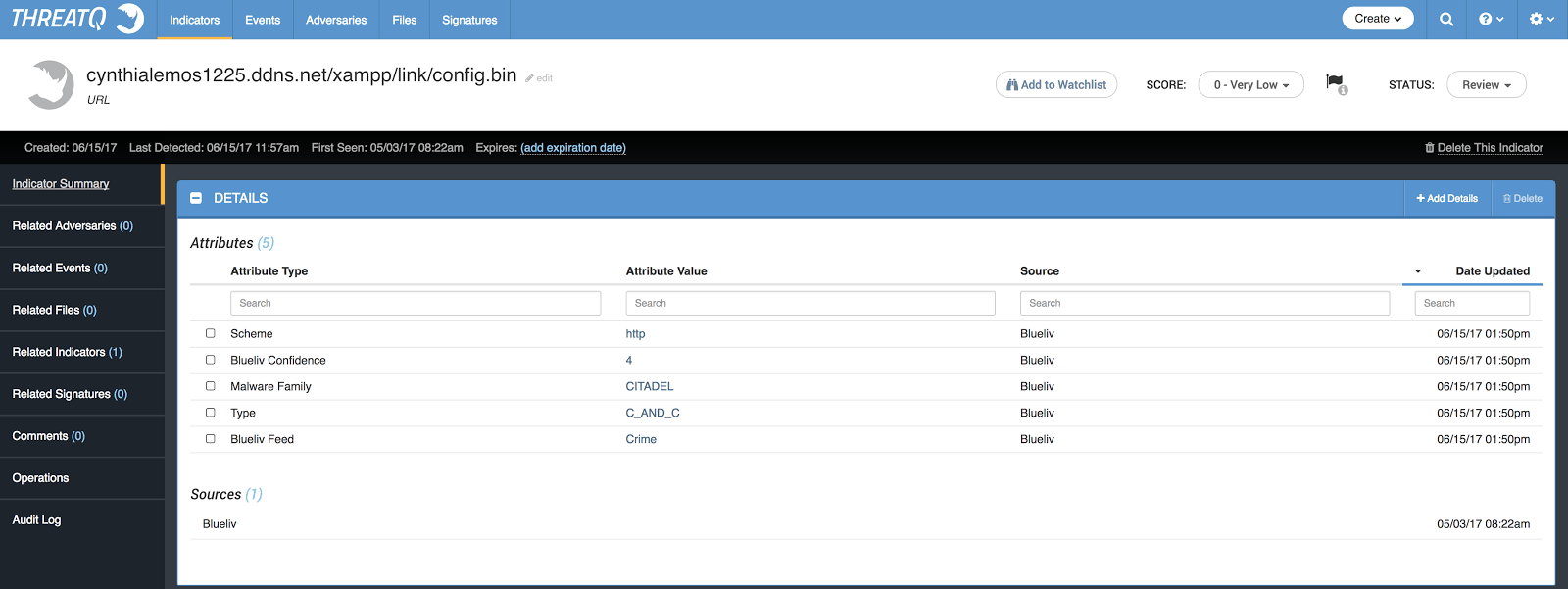
Figure 4: Additional attributes found for an indicator that was not picked up by the open source feed
In another example of overlapping sources, we have information on an IP Address that was picked up by both Blueliv and Malware Domain List. In this case, both intelligence feeds contributed to the list of attributes seen in Figure 5. However, as you can see, the Malware Domain List only provided a short description and the ASN. As in the previous example, Blueliv was able to provide much more information on the IP Address, as well as confirm the ASN provided by the Malware Domain List Feed.
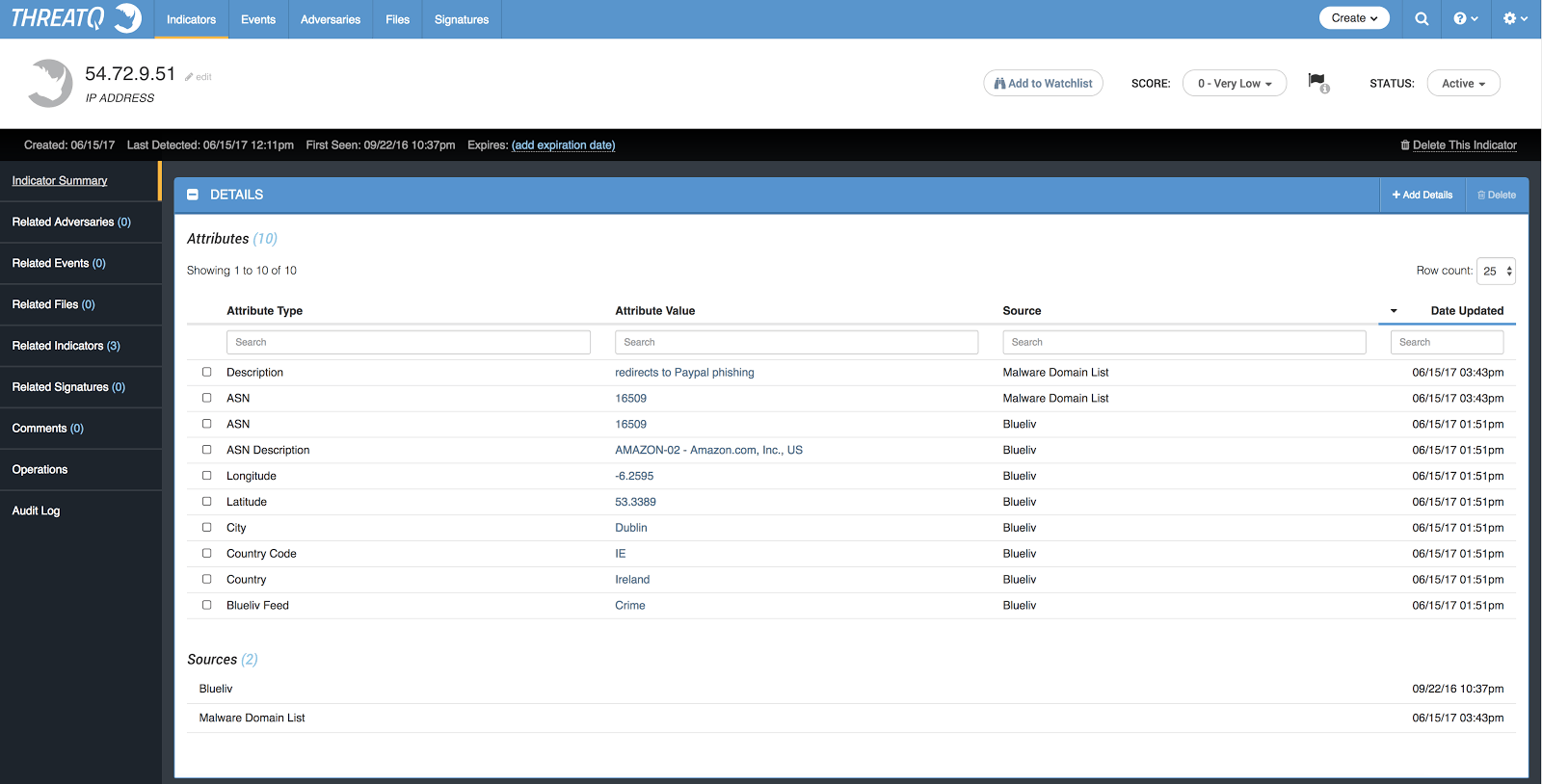 Figure 5: Shows an indicator with overlapping sources, along with attributes from both sources
Figure 5: Shows an indicator with overlapping sources, along with attributes from both sources
If we scroll down on the page we can see the related indicators as shown in Figure 6. Here we can see all of the domains related to the IP Address. This is great information to have as you would not be able to relate the URL/IP/FQDN indicators easily without ThreatQ. We can also click on the related items to view information on them.
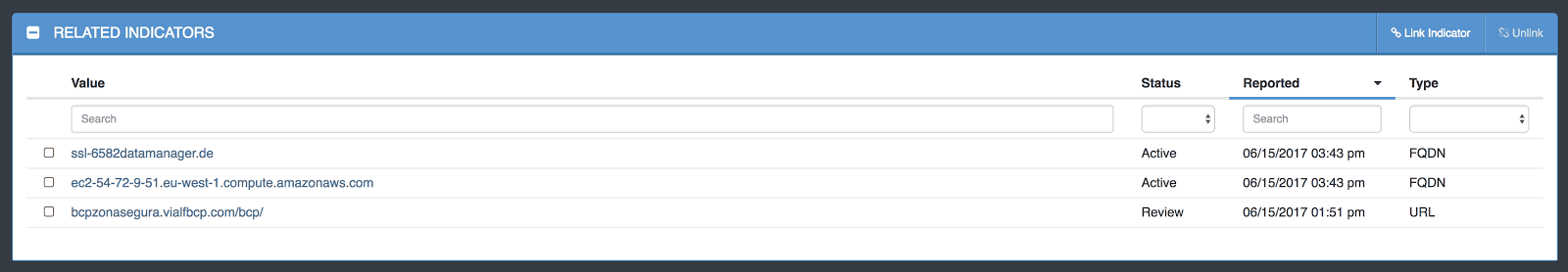
Figure 6: Shows an indicator’s related indicator
Conclusion
Using Blueliv with the ThreatQ threat intelligence platform can provide a major advantage when fighting malicious threats. The information it provides will not only help enhance your system’s defenses, but also augment your knowledge base on a threat. Paired with ThreatQ’s scoring, open source feeds, and commercial feeds, Blueliv adds valuable data that will help protect your organization and allow you to gain even greater value from your existing threat intelligence investments.

0 Comments