ThreatQuotient Content Library
At A Glance & Datasheets
Scoring and Expiration Lifecycle
DoD Zero Trust Architecture
ThreatQ TDR Orchestrator
DataSheet
Air-Gapped
DataSheet
ThreatQ by Industry
ThreatQ for
Education
ThreatQ for
Government Agencies
ThreatQ for
Manufacturing
ThreatQ for
Transportation
ThreatQ for
Energy
ThreatQ for
Entertainment
ThreatQ for
National Cyber Agencies
ThreatQ for
Technology Companies
ThreatQ for
Critical Infrastructure
ThreatQ for
U.S. Government
ThreatQ for
Healthcare
ThreatQ for
Retail & Hospitality
ThreatQ by Role
ThreatQ
for CISOs
ThreatQ
for SOCs
Customer Success Stories
Customer Success Story: Sesame it
Customer Success Story: Thales
ThreatQ Case Studies
ThreatQ Use Cases
Whitepapers and Reports
Buyer’s Guide to Threat Intelligence Platforms
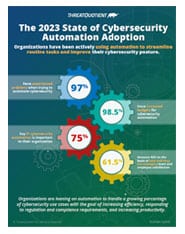
State of Cybersecurity 2023 Report
State of Cybersecurity 2021 Report
SANS 2022
Product Review
Regulations and Compliance
Enhancing Cyber Resilience: How ThreatQ Aligns with NIS2 Directive Requirements
Empowering Financial Institutions to Meet DORA Requirements
Partner Briefs
ThreatQuotient and PwC Threat Intelligence
ThreatQuotient and Brandefense
ThreatQuotient and alphaMountain
ThreatQuotient
and Quaxar
ThreatQuotient
and CyberSixgill
ThreatQuotient
and Dataminr
ThreatQuotient
and TeamT5
Partner Integration
Program Overview

ThreatQuotient
and OPTIV
ThreatQuotient
and Cisco