Victimology: Target Association
POSTED BY RYAN TROSTIn a previous life, I managed two SOCs with 40+ analysts each, where a large component of the team was dedicated to threat intelligence, more specifically victimology. Admittedly I am by no means an expert at victimology. However, surrounded by several colleagues who had been formally trained by the Air Force, I picked up a couple fundamental approaches. My goal in this blog series is to expose a small fraction of the value associated to victimology by:
- analyzing the recipients of a long-term spear phish campaign
- performing some victimology timeline analysis
- performing some rudimentary adversary attribution using victimology
I am also going to structure each blog into a logical workflow of:
- create a hypothesis
- how-to carve out the data
- now what to do, given the results
So let’s get started with a scenario involving the latest wave of targeted spear phish coming from [robertwanger [at] aol.com]. A colleague at a competitive but friendly company learned of it, and advised me to look into it as well. At first glance, you immediately note the accidental or purposeful transposing of “n” and “g” in the last name. A handful of adversaries love to use famous actors/actresses in their attacks – usually with a Sci-Fi theme but in this case Robert Wagner, the famous 80’s actor. It’s hard to tell if that was intentional, but always worth noting to help frame the picture of the adversary and potentially look for other, similar email addresses.
Hypothesis – I bet my company was targeted by “RobertWanger [at] aol.com” as well.
A quick cursory search does identify several targeted emails – luckily blocked by technologies. Now in my experience this draws a line in the sand between Security Analysts and Threat Intelligence Analysts. A Security Analyst sees a technology blocked it and as they have 1,000s of other alerts to research they close the case and move on to the next; whereas, a Threat Intelligence Analyst knows it’s just a matter of time before the adversary does make it through and therefore its worth spending a couple of hours to dive in deeper to try and identify a few tactics, techniques and procedures (TTPs).
How to? There are numerous ways to help draw out some of these motivations but I decide to focus on victimology within a node link analysis graph. First, I need to flag all emails sent by ‘robertwanger’ as a spear phish attack – so I run a search against my logs and import those into my TIP to see if there are any correlations with other internal or external intelligence. Done and done. The resulting graph looks like this:
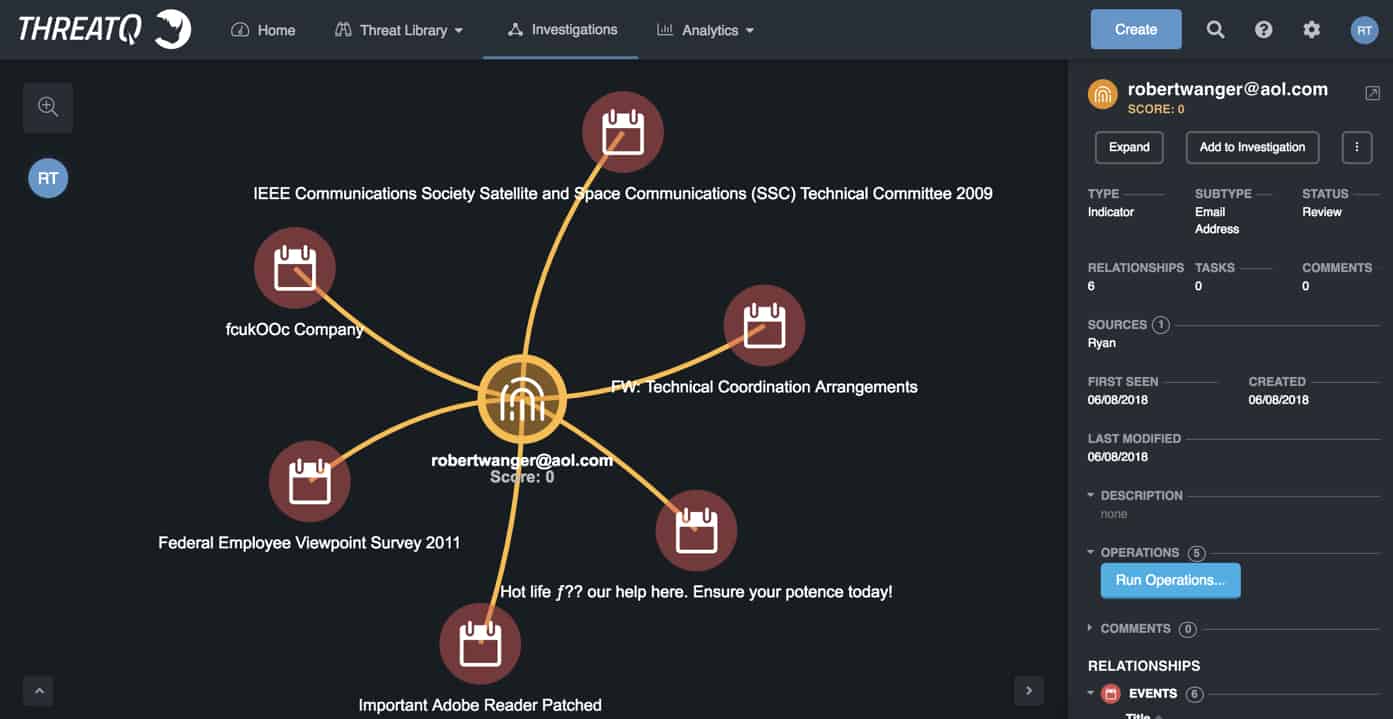
Each spear phish event, in this case, represented by a Calendar icon, has several additional characteristics associated with it including Indicators, Attributes, etc. Typically, I would expand each event’s indicators to see if there were any overlap. But as this blog is focused on victimology, I am going to jump to that. In line with my Type A OCD personality, I reposition each Event to be in chronological order from left to right creating somewhat of a 2-dimensional link analysis + timeline analysis visualization. Looking at the various spear phish subjects there is quite a range of themes – so that’s not an analytical direction I will spend much time pursuing.
In order to perform victimology, you need to import employee email addresses into your TIP – and it’s worth pointing out I would ONLY do this with an on-premise TIP where you are not authorizing the vendor access to that information. There are a couple of different ways to import an employee’s email address including manual (do yourself a favor and delegate to an intern), pull directly from Active Directory, export Global Address List (GAL) and script the import via API/SDK. Another super important note – you not only want to import the employee’s email address but any additional context that will significantly help with victimology hunting including job title, department, geographic location, manager’s name, etc. Admittedly, you are at the mercy of your company’s Human Resources documentation and the ability to tie that into system administration infrastructure. But with software platforms like PeopleSoft, Namely, ADP and GSuite, those integration data fields are becoming more and more standard.
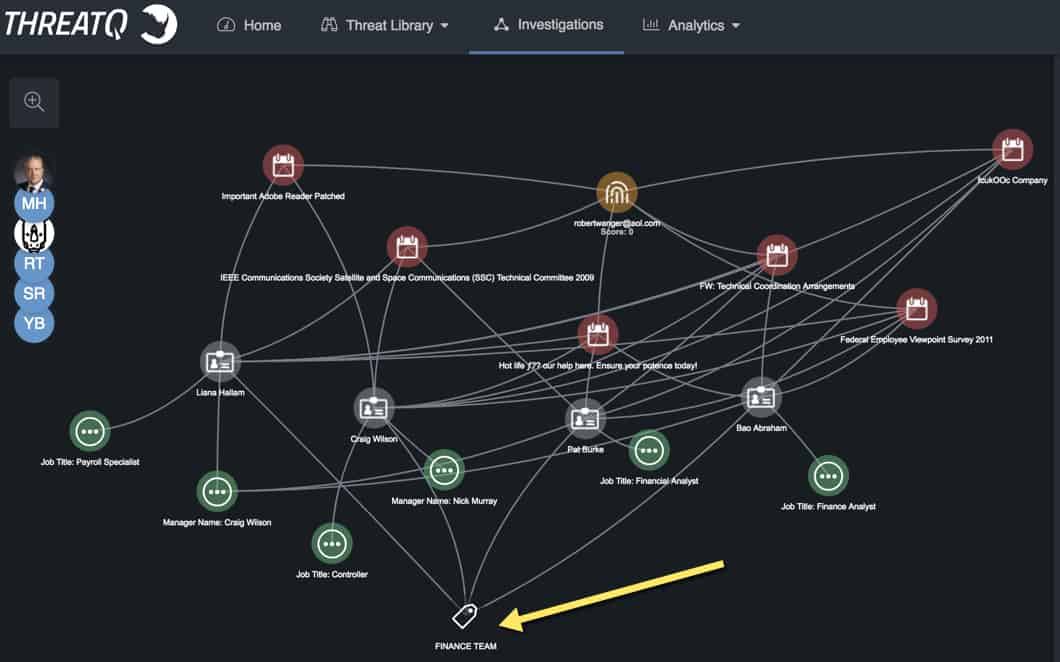
I imported employees as ‘Identities’ within ThreatQ and manually associated each spear phish with the recipients. Now that all the data is prepped, it’s time to roll up my sleeves and perform some victimology research. A quick right-click -> Expand -> Identities on each of the spear phish events displays the recipients of the individual attacks, immediately recognizing the targeting overlap across attacks.
My organization is large enough that I don’t know everybody in the company by name so displaying some of those additional employee characteristics is critical to identify any unbeknownst associations. In the below graphic, I right-clicked on each Identity and selected Expand -> Tags to display job title, manager’s name and department. There isn’t a direct tie to job titles or managers, but a small victory as all the spear phish recipients across the attacks are part of the Finance Team.
Now what? There are a couple of things you can do with this information, including:
- Now that we know this attacker is likely motivated by financial gains given their target list – time to build an adversary profile/dossier!
- Even though our defenses blocked the delivery of the emails, I would proactively notify the targets and walk them through the analysis as follows:
- spear phish are coming from suspicious AOL accounts
- 2 of the 6 spear phish have off-the-wall subjects
- 1 of the 6 has a “FW:” in the subject line which implies that the adversary knows that this technique helps coax the target to open the spear phish
The purpose of this activity is a bit of ‘employee email vigilance’ to try and educate the targets as to what to look for in future emails. I’m relatively confident at some point our defenses will fail and we’ll have to rely on employees (are our weakest link but also our greatest asset) not to click.
- Ask the malware team to analyze each email delivery – attachment or URL. This will help determine the adversary’s level of sophistication, or lack thereof (since this time the emails were blocked).
Want to know more? Read the second post in the series, “Timeline Analysis to Identify Campaign Attacks”

0 Comments