Get Smarter About Vulnerabilities
POSTED BY JULIAN DEFRONZOIntroducing CVE Indicator Types
While it may seem like you’re constantly hearing about a new attack method or cyber threat in the world, in reality, hackers are reusing exploits and tools as part of their campaigns. In fact, in most cyberattacks, criminals exploit some sort of security weakness — a vulnerability that is already known and for which a patch is currently available.
With the release of 3.1, the ThreatQ Threat Library now supports the inclusion of vulnerability data using the Common Vulnerabilities and Exposures (CVE) standard. This enhances the Threat Library to incorporate information on vulnerabilities from multiple threat intelligence providers to identify exploits involved in current ongoing campaigns and better protect against these types of attacks.
National Vulnerability Database Integration
In addition to supporting CVE indicators, as part of 3.1 we’ve also expanded functionality to many existing commercial intelligence feeds that include CVE and vulnerability data. The ThreatQ threat intelligence platform now also supports an integration with the National Vulnerability Database (NVD) that pulls the entire CVE database into ThreatQ so that analysts can start tracking existing and new vulnerabilities while also providing additional context around a specific vulnerability.
The NVD provides access to vulnerability analysis on affected products/vendors and risk impacts based on the Common Vulnerability Scoring System (CVSS). The ThreatQ threat intelligence platform supports this data as attributes tied to the CVE indicator (Figure 1). These attributes can be used in your custom scoring profile to bubble up those vulnerabilities that are most important to you and aid in prioritization of remediation (Figure 2).
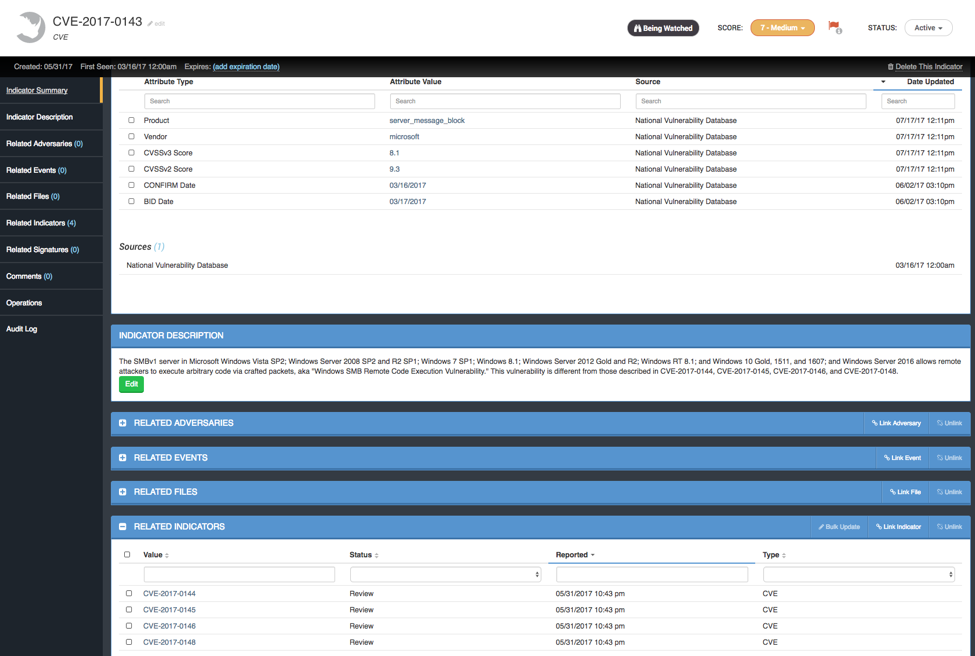
Figure 1: CVE indicator details
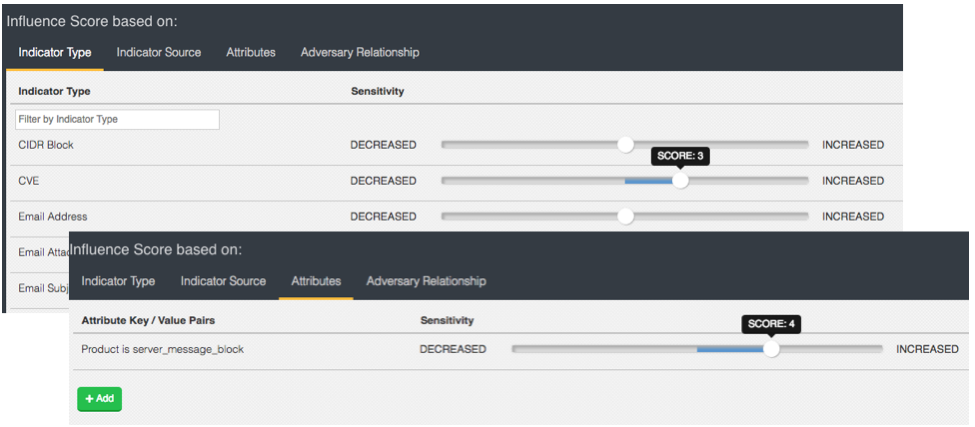
Figure 2: Scoring rules based on CVE details
Bringing Threat Intelligence and Vulnerability Management Together
With the number of vulnerabilities being discovered and announced on the rise, it’s hard for security teams to prioritize patching. By marrying threat intelligence and vulnerability data together, security teams have more data and context to form an action plan to address specific security measures. Combining threat intelligence with vulnerability management provides an extra level of information about risks that can be used for prioritization and to make informed decisions that strengthen security posture.
In future blog posts, we will take a deeper dive into other integrations in the vulnerability management space that further enhance ThreatQ’s self-tuning Threat Library and Open Exchange capabilities and your ability to protect against known security weaknesses.
To learn more, download our Vulnerability Application Note.

0 Comments